Scalar i6000 User Access
Overview
User privilege levels are manually assigned to user accounts created within the library. Controlling access to screens and operations within the library preserves the integrity of the library and its data.
After a user account has been created, administrators can modify the account settings, such as the password and role. You cannot modify the user name. Instead, you will need to delete the user account and create a new one.
User Roles
Three types of roles are defined in the library.
| User Role | Description |
|---|---|
|
|
Have access to all library configuration and operation functionality and can set up user and administrator accounts. The library ships with a default administrator account. The user name for the default administrator account is admin and the password is password. You cannot modify or delete the user name for the default administrator account, but you can modify the password. |
| Users | Have access to one or more assigned partitions and can perform operations within a partition. A user cannot perform configuration changes and is restricted to operations only. |
|
|
Has access to the same functionality as administrators with the exception of user access configuration. Each library has only one service account. |
User Privileges
-
25 user sessions (users and administrators) can be active at one time.
Note: Up to 32 admin user sessions can be active when using the Web Services API.
-
By default, a 5 minute lockout occurs after a user fails to successfully log in 5 times.
Default password settings can by changed under Login Rules.
Note: The library does not keep track of incorrect login counts and lockout times after the library is power-cycled or rebooted.
- The same user can be logged in to a library from multiple locations.
- Clicking the close button (X) in the upper-right corner of your browser closes the browser window but does not close the user session. This can cause a user to have multiple open sessions in the WebGUI. To avoid having multiple sessions open for the same user, log off from the WebGUI before closing the browser.
- All users are logged out automatically after a configurable period of inactivity. The default user session timeout period is 15 minutes, but administrators can change the user session timeout to a value from 5 minutes to 24 hours.
- When a service user logs in, all other active users are automatically logged out to prevent command interference. In addition, event tickets are not sent/emailed when Service is logged in.
- For security purposes, an administrator can prevent a service user from logging on to the library remotely, from either the WebGUI or through the service port. The service user will still be able to log on to the library from the LUI.
Layout
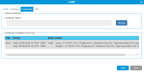
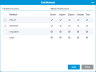
Displays a list of all users created for your library.
| Column | Description |
|---|---|
| Name | User name. |
| Role | Role assigned to user (Admin, User, Service). |
| Sessions | Number of library sessions user is currently logged into. |
| LDAP Login | LDAP user (yes or no). |
Lists details for a user highlighted in the North Panel.
| Detail | Description |
|---|---|
| Name | Selected user name. |
| Role | Role assigned to selected user (Admin, User, Service). |
| Sessions | Number of library sessions selected user is currently logged into. |
| LDAP Login | Selected user can use LDAP (yes or no). |
Shows configuration details on the user, admin, and service user roles.
| User/Admin | |
|---|---|
| Detail | Description |
| LUI Access | Login status of the Local User Interface (LUI). Open access, password required, or PIN required. |
| LDAP Support | LDAP enabled or disabled. |
| Session Timeout | Amount of time a user must be inactive before the session is ended. |
| Multi Factor Authentication | MFA enabled or disabled. |
| Access Restrictions | User and administrator accounts to allow access only from defined IP addresses is enabled or disabled. |
| Service | |
|---|---|
| Detail | Description |
| License | Service license active or inactive. |
| Remote Access | Service remote login access is enabled or disabled. |
| Remote Access - Access Window | Time period a service user has to remotely login before access is disabled. |
| Remote Access - Access Grant | Timestamp when the service remote login access window began. |
| Local Access | Local service port login access is enabled or disabled. |
| Local Access - Access Window | Time period a service user has to log into the local service port before access is disabled. |
| Local Access - Access Grant | Timestamp when the local service port access window began. |
| Reverse Tunnel | Reverse tunnel access is enabled or disabled. |
| Reverse Tunnel - Access Window | Time period a reverse tunnel needs to be established before the tunnel access is no longer granted/authorized. |
| Reverse Tunnel- Access Grant | Timestamp when the reverse tunnel access window began. |
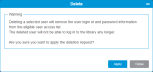
Provides options for user configuration and actions.
| Configuration | |
|---|---|
| Add | Allows you to set up a user. |
| Modify | Allows you modify a user. System configured users are not available for modification. |
| Delete | Allows you to delete a user. System configured user are not available for deletion. |
| LDAP | Allows you to set up Lightweight Directory Access Protocol (LDAP). LDAP can be used to authenticate user credentials and assign access levels to the system. |
| Entitlement | Allows you to set up which partitions a user can access. |
| Settings | Allows you to configure system-wide user details. This includes session timeouts, service access and user access to your library's LUI. |
| MFA | Allows you to set up Multi-Factor Authentication (MFA). MFA requires a user to enter both a password and authentication code to access the system. |
| Restrictions | Allows you to restrict remote login access to user and administrator accounts on defined IP addresses. |
| Actions | |
|---|---|
| End Session | Allows you to manually end a user session. |
| Policies | |
|---|---|
| Login Rules | Allows you to manually configure user password login rules. |
Tasks
Operations
You can add two types of users: user and administrator. Administrators have access to all features and functions, while users have some restrictions on what they can configure.
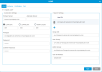
- From the Navigation panel, select User Access.
-
In the Operations panel, click Add.
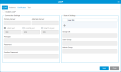
Item Description Action User Name Allows you to create a user name.
User names must meet the following criteria:
-
1-64 characters long.
-
User names are not case sensitive.
-
User names must remain unique and must not match technical or reserved names.
-
Any alpahnumeric characters and spaces are allowed.
-
The following special characters are permitted: ._@!#$&()+,:;=[]{}|^-
-
Back tick (`) and tilde (~) are not permitted.
-
Leading or trailing spaces are not permitted.
Enter text. Role Allows you to select the type of user you want to create:
- user
- administrator
Select the desired role from the drop-down menu. Password Allows you create a password. Current password creation rules can be reviewed and configured under Login Rules.
-
Passwords are case sensitive.
-
Passwords support 8 to 64 printable ASCII characters except for the tilde (~) and backtick (`) characters.
-
Leading and trailing space ( ) characters are not supported.
Enter text. Confirm Password Validate password created in the Password field. Re-enter text. -
-
Click Apply to save your settings.
-
Click Close to exit the window.
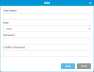
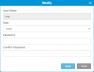
- From the Navigation panel, select User Access.
- In the North Panel, click the checkbox next to the user you want to modify.
-
In the Operations panel, click Modify.
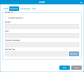
Item Description Action User Name Users assigned the Admin role can have the User Name changed.
Users assigned the User role cannot be edited. If you want to change this field, you must delete the user profile and create a new one.
If the user role is Admin, modify the User Name. Role Allows an administrator to select the type of role:
- user
- administrator
Select the desired role from the drop-down menu. Password Allows a user or admin to change a password. Current password rules can be reviewed and configured under Login Rules.
Note: After the initial installation of the library, the initial Admin user password cannot be changed to the default password of "password". Admin users created after the initial installation have no password restrictions.
Enter text. Confirm Password Re-enter text.
-
Click Apply to save your settings.
-
Click Close to exit the window.
Lightweight Directory Access Protocol (LDAP) is the industry standard Internet protocol that provides centralized user account management. The library supports LDAP Directory servers based on Microsoft Active Directory and Novell eDirectory. You can configure the Lightweight Directory Access Protocol (LDAP) settings any time after the initial library configuration. Once you enable and configure LDAP, you can view your current LDAP settings using the LDAP menu.
Note: Active Directory no longer requires Windows Services for Unix 2.5.
LDAP and AD Terms
Common Name (CN)
An attribute that is commonly used to identify the name of Organizational Unit (OU).
Example
The SysAdmin group would have cn=sysadmin.
Domain Component (DC)
The domain of the directory, which often identifies the organization or company.
Example
Mycompany.com would have a domain of dc=mycompany,dc=com.
Distinguished Name (DN)
A pathway that tells LDAP where information is stored in its directory. LDAP reads the pathway from right to left, with the farthest right components providing the domain of the directory and the farthest left component providing the information for which LDAP is looking.
Organizational Unit (OU)
A component used to organize information into a hierarchical structure. OUs can be used at multiple levels within the LDAP or AD directory, such as to act as a larger Group bucket that then holds individual group OUs.
User ID Attribute
The user ID that is associated with the user object in the LDAP or AD hierarchy. For LDAP, this attribute is commonly the uid. For AD, this attribute is commonly SAMAccountName.
Figure 1: Sample LDAP Configuration
Enabling LDAP allows existing user accounts residing on an LDAP server to be integrated into the library’s current user account management subsystem. User account information is centralized and shared by different applications, simplifying user account management tasks.
The remote client and operator panel do not allow you to create, modify, or delete user account information on an LDAP server. This must be done by the directory service provider.
The following groups must be created on the LDAP server to enable remote login on the library:
| Group | Description |
|---|---|
| Library User Group | Assign users to this group who need user privilege access to the library |
| Partition Groups | For LDAP users with user privileges, access to library partitions is determined by group assignment on the LDAP server. Groups must be created on the LDAP server with names that match the library partition names (names must match but are not case sensitive). Users with user privileges must be assigned to these groups on the LDAP server to have access to the corresponding partitions on the library. |
| Library Admin Group | Assign users to this group who need administrator-privilege access to the library. LDAP users with administrator privileges have access to all partitions and administrator functions and do not need to be assigned to partition related groups on the LDAP server. |
Additional Information
- Groups must be created on the LDAP server with names that correspond to the library partition names.
- User and library groups must reside in or below the group context.
- User names and group objects must be in LDAP Distinguished Names formats.
For OpenLDAP 2.4:
- You must install and run OpenLDAP 2.4 or later.
- The supported Objects in OpenLDAP 2.4 and later are of type “Person” or derived objects, and the group Objects must be of type “GroupOfNames.”
- OpenLDAP must be compiled with Overlay Support and requires the installation of “memberOf” overlay. More information can be found in the man pages of OpenLDAP with the “man slapo-member of” command.
- From the Navigation panel, select User Access.
-
In the Operations panel, click LDAP.
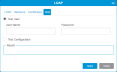
Item Description Action Enable LDAP Activates LDAP setting fields.
Note: Disabling LDAP will not cause you to lose any entered and saved settings. If you need to change any settings prior to re-enabling LDAP, you will need to enter the necessary changes to each field.
Select the check box to enable LDAP. Deselect the check box to disable LDAP. Primary Server Allows you to enter the address to the server that is first accessed for user LDAP information. Enter text. Alternate Server Allows you to enter the address to a server to access user LDAP information if the primary server is unavailable. Enter text. LDAP Port Basic connection type. Default port is 389. Select the radio button. LDAPS Port Secure connection type. Default port is 636. Select the radio button. StartTLS Port Default port is 389. Select the radio button. Principal The user name of the user with permissions to search for the user trying to use LDAP to login.
Note: The principal must be a fully qualified name to be accepted.
Enter text. Password The password of the principal. Enter text. Confirm Password Re-enter text. User DN This is a fully qualified LDAP DN (distinguished name) and is used as the base to search for a user's login credentials. You can search for a user in the context specified and all contexts below it. Click the + to enter the user DN. Group DN Use this field to search and discover what groups a user is a member of. Only groups which are in the group context are considered for library access. Enter text. User Group The group associated with the library. A user that belongs to the library user access group is granted user level permission to access the library. For a user to manage a partition, that user must also be a member of a user group with the same name as the library partition in question.
If a CN with users in it is not available, use a name of a group the users are members of. An OU will not work.
Note: The User Group only requires a simple name of the group.
Enter text.
Admin Group The group associated with the library administrator, equivalent to the local administrative user privilege level. Any member of this group has administrative privileges.
If a CN with users in it is not available, use a name of a group the users are members of. An OU will not work.
Note: The Admin Group only requires a simple name of the group.
Enter text.
Note: Non-admin library users also need to be members of the groups that match the partition names for which they are granted access. These group names do not need to be specifically listed anywhere in the LDAP setup on the library. When user logins are validated during login, their group memberships for partition access are validated automatically.
-
Click Apply to save your settings.
- Select the Test tab and run a test on your settings to ensure they are configured properly.
-
Click Close to exit the window.
Kerberos is a secure method for authenticating a request for a service in a computer network. It is designed to provide strong authentication for client/server applications by using secret-key cryptography.
Note: The Kerberos tab is only available when the Enable LDAP check box is selected.
- From the Navigation panel, select User Access.
- In the Operations panel, click LDAP.
-
Select the Kerberos tab.
Item Description Action Enable Kerberos Activates the Kerberos security protocol. Select the check box. Realm Name of instance. Typically the realm is the same as your domain name, only in all upper case letters. Enter text. KDC The Kerberos Key Distribution Center (KDC). This is a network service that supplies session tickets and temporary session keys to users and computers within an Active Directory domain. The KDC runs on each domain controller as part of Active Directory Domain Services (AD DS). Enter text. Domain Mapping The fully qualified DNS name of the machine that provides the Kerberos service. Enter text. Keytab File A keytab is a file containing pairs of Kerberos principals and encrypted keys (which are derived from the Kerberos password). You can use a keytab file to authenticate to various remote systems using Kerberos without entering a password. However, when you change your Kerberos password, you will need to recreate all your keytabs.
Keytab files are commonly used to allow scripts to automatically authenticate using Kerberos, without requiring human interaction or access to passwords stored in a plain-text file. The script can use the acquired credentials to access files stored on a remote system.
Click Browse to navigate to where the keytab file is located. -
Click Apply to save your settings.
-
Click Close to exit the window.
LDAP communications are not encrypted by default and you may want to use LDAPS for greater security. You can do this by using an SSL certificate to provide security for any LDAP data transfers.
- From the Navigation panel, select User Access.
- In the Operations panel, click LDAP.
-
Select the Certificates tab.
Item Description Action Certificate Name Displays the LDAPS certificate name.
Click Browse to navigate to where the LDAPS certificate is located. -
Click Apply to save your settings.
-
The Certificate Installation Summary contains the following information regarding the loaded LDAP certificate:
Item Description Type Specifies the certificate type. Types include server, root, and client.
Validity Time period the certificate is valid for. Status Valid or invalid. Details Contains information regarding the certificate issuer, such as organization name, location, and contact information. -
Click Close to exit the window.
When setting up LDAP you may want to test your settings to ensure they work properly. On the Test tab, you can test a specific user or your configuration settings.
Note: The Test tab is only available when the Enable LDAP radio button is selected.
- From the Navigation panel, select User Access.
- In the Operations panel, click LDAP.
-
Select the Test tab.
Item Description Action Test User Allows you to test a specific user's logon credentials.
Select the radio button. User Name Allows you to enter a user name. Enter text. Password Allows you to enter the user's password. Enter text. Test Configuration Allows you to test the configuration settings you entered on the LDAP tab. Select the radio button. -
Click Apply to save your settings.
-
Click Close to exit the window.
This window allows an administrator to configure partition-specific access restrictions for each user.
- From the Navigation panel, select User Access.
- Select a user from the North Panel
-
In the Operations panel, click Entitlement.
Item Description Action Partition Access Displays a list of available partitions.
Select the check box next to the partition(s) you want to enable media access. Deselect the check box next to the partition(s) you want to disable media access. Media Restrictions Lists the five (5) types of access to media for the partition:
- Move - ability to move media from/to the selected partition
- Import - ability to import media into the selected partition
- Export - ability to export media from the selected partition
- Unload - ability to remove media from drives associated with the selected partition
- Test - ability to run EDLM scans on drives in the selected partition.
User the Partition Access check box to disable/enable media access. -
Click Apply to save your settings.
-
Click Close to exit the window.
This window allows you to set up specific access properties for the three different user roles that can access your library: user, administrator and service.
- From the Navigation panel, select User Access.
-
In the Operations panel, click Settings.
Item Description Action Session Timeout Allows you to set the amount of time a user must be inactive before the session is ended. This timeout applies to both admin and user accounts.
Note: Applied session timeout changes do not implement in the i6000 library until the WebGUI performs a command that re-initializes the WebGUI. The WebGUI is re-initialized when the white loading wheel appears in the WebGUI. An example of a command where re-initialization occurs is performing inventory. Once re-initialization of WebGUI completes, the requested new session timeout change occurs.
Select the desired user session timeout from drop-down menu.
Service Access - Enable Remove Service User Login Access.
Allows a service user to access your library remotely.
Note: Enable remote service user login is disabled by default for 779 library firmware and above.
Select the check box to enable the Service login. Deselect the check box to disable the Service login. Service Access - Enable Reverse Tunnel Reverse tunneling allows a Quantum Service access to the library through a secured connection. To enable the reverse tunnel, the following process occurs:
-
Library administrator sets an access window time period for a reverse tunnel and enables the tunnel in the WebGUI. A reverse service tunnel request is made to Quantum Service through the CBA portal (see Cloud-Based Analytics).
-
The library or CBA administrator approves the request in the CBA portal.
-
Once approved, Quantum Service makes a secured connection to the library using CBA infrastructure. Quantum Service can connect and disconnect to the library during the specified access window.
-
When the specified access window expires, all connections from Quantum Service to the library are closed. A new reverse tunnel request must be made.
Select the check box to enable the service tunnel.
Deselect the check box to disable the service tunnel.
Service Access - Access Window The access window determines the time period that Quantum Service can access the library through the enabled remote server user login and/or reverse tunnel.
The time period begins once the remote server user login and/or service tunnel is applied.
Once the access window expires, a new request and approval must be made to establish a reverse tunnel and/or remote service user login.
Select the desired reverse tunnel access time from the drop-down menu.
-
-
Click Apply to save your settings.
-
Click Close to exit the window.
Multi-Factor Authentication (MFA) is an authentication method that requires a user to successfully enter both a password and an authentication code before access to the library is allowed.
The authentication code is a temporary passcode that is generated by a Time-based One-time Password (TOTP) algorithm. A user generates authentication codes using an authenticator application on a client device.
Authentication Client Device
MFA requires an authenticator application be downloaded on a client device, such as your mobile phone. Once installed, the authenticator application is validated with a shared secret code generated by the library. The authenticator application will then generate authentication codes that allows a user to log into the library and administrators to enable and disable MFA.
Authentication codes are one-time use and time-limited to 90 seconds.
Additional Information
- MFA is enabled or disabled for all library users. Individual users cannot have MFA enabled or disabled.
- Quantum strongly advises using Network Time Protocol (NTP) to ensure that the library and the authentication client device share the same time. A time drift on the library could prevent authentication code generated from the authentication client device from working. To set NTP on the library, see Setup Date and Time.
- LDAP user logins do not suport MFA.
- An administrator logged into the library using LDAP cannot disable MFA. The administrator must be logged into the library using a username and password from the User Access section of the library.
- MFA configuration is saved and can be restored from the library configuration (see Save or Restore the Library Configuration). Quantum recommends saving the library configuration once MFA enablement is complete.
-
Quantum strongly advises turning off remote service login. A service user is never required to use MFA. Leaving the remote service login enabled is a security risk. To disable remote service login, see User Access Settings.
- From the Navigation panel, select User Access.
-
In the Operations panel, click MFA.
-
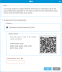
Select the Enable Multi Factor Authentication check box. The Time-based One-time Password (TOTP) is selected and a shared secret code is generated by the library. The shared secret appears in the Shared Secret box in a numerical and QR code format.
-
If you have not already done so, download an authenticator application to a client device.
- An example of an authenticator application would be Microsoft Authenticator or Google Authenticator.
- An example of a client device would be a mobile phone or tablet.
-
Open the authenticator application on your client device. Scan the QR code or enter the shared secret code generated by the library in step 3. The authenticator application will now generate a 6 digit authentication code that changes every 30 seconds.
-
Enter the 6 digit authentication code generated by the authenticator application in the Authentication Code field. If the code is accepted, MFA will be enabled. If the code is not accepted, MFA will not be enabled.
Note: The authentication code must be entered and applied within 90 seconds after being generated by the authenticator application. If more than 90 seconds have passed, you must generate a new authentication code to successfully enable MFA.
-
Click Apply. MFA is now enabled on the library. All subsequent login requests will be required to configure MFA and provide the additional authentication code during system login attempts.
To access the library, users will now have to enter an authentication code in addition to username and password
Note: Only a library administrator can disable MFA.
- From the Navigation panel, select User Access.
-
In the Operations panel, click MFA.
- Deselect the Enable Multi Factor Authentication check box.
-
Disabling MFA requires an authentication code generated from the authentication application. Enter the 6 digit authentication code generated by the authenticator application in the Authentication Code field.
Note: The authentication code must be entered and applied 90 seconds after being generated by the authenticator application. If more than 90 seconds has passed, you must generate a new authentication code to successfully disable MFA.
- Click Apply. MFA is now disabled on the library.
Multi-Factor Authentication Guidelines
-
Current Users
A current user will log into the library using the current assigned User Name and Password.
New Users
If a new user needs access to the library the library administrator creates a new user (see Add a User). The new user will then log into the library using the User Name and default Password created by the administrator.
-
After the new user logs on, a dialog box will appear containing a shared secret code in numerical and QR code format:
-
To complete the login process, the user must do the following:
- Install an authenticator application on a client device.
- Scan the QR code or enter the shared secret code into the authenticator application. The authenticator application will now generate a 6 digit authentication code that changes every 90 seconds.
-
Current Users
Using the authenticator application, the user enters an Authentication Code and clicks Apply to complete the login.
New Users
Using the authenticator application, a new user enters an Authentication Code and clicks Apply. The Password Change Request dialog then appears, prompting the new user to change the default password created by the library administrator.
Users
If a user loses the client device (such as a mobile phone) with the authentication application installed, a library administrator will need to delete the user and create a new user profile.
Default Administrator
If the default administrator (the original admin account created when the system was installed) loses the client device with the authentication application installed, the default administrator can use the Local User Interface (LUI) to disable MFA and gain access to the library. The disable MFA feature is located at Admin > Maintenance > Library > Disable MFA in the LUI.
A service user does not require MFA authentication. If MFA is enabled, there are two options for the service user to access the library:
- Service user can access the library through the Local User Interface (LUI).
- For remote access to the library, the administrator can enable remote service login. Once the service user is finished working in the library, the administrator must disable remote service login (see User Access Settings).
Allows you to restrict remote login library access for user and administrator accounts on defined IP addresses.
Note: This feature is not available for service users.
-
From the Navigation panel, select User Access.
-
In the Operations panel, click Restrictions.
Note: For IP restrictions to be enabled, no users can be selected in the North panel.
Item Description Action Current IP Source IP Address Indicates your current IP Address. When enabling IP restrictions, your IP address must be in the IP Address Permissions list. To copy your current IP Address to the IP Address Permissions List, click on the IP address. In IP Address Permissions, click + to open an IP Address field. Right-click your mouse over the field and select Paste. Enable Login Restrictions Allows you to enable or disable IP login restrictions. When enabled, only users and administrators with IP addresses in the IP Address Permissions List will have remote login access to the library. Select the check box to enable IP Address login restrictions.
Deselect the check box to disable IP Address login restrictions.
IP Address Permissions Allows you to add or delete IPv4 and IPv6 addresses from the permission list. A maximum of 25 IP addresses can be added to the permission list.
Note: The host IP address must be in the permission list.
Click + to add an IP address to the list.
Click the trash icon to delete an IP address from the list.
-
Click Apply to save your settings. The Apply button will be disabled if login restrictions are enabled and your IP address is not in the IP permissions list.
Policies
Administrators can configure the login rules for library user passwords.
- From the Navigation panel, select User Access.
-
In the Operations panel, click Login Rules.
Item Description Default Setting Setting Range Minimum Characters Minimum password length.
8 -
Minimum Setting: 8
-
Maximum Setting: 64
Maximum Characters Maximum password length.
64 -
Minimum Setting: 8
-
Maximum Setting: 64
Minimum Uppercase Password requires a specific number of upper case characters (A-Z). 0 -
Minimum Setting: 0
-
Maximum Setting: 64
Note: The number of minimum uppercase characters cannot exceed the defined maximum password length.
Minimum Lowercase Password requires a specific number of lower case characters (a-z). 0 -
Minimum Setting: 0
-
Maximum Setting: 64
Note: The number of minimum lowercase characters cannot exceed the defined maximum password length.
Minimum Digits Minimum number of number digits (0-9) required in password:
0 -
Minimum Setting: 0
-
Maximum Setting: 64
Note: The number of minimum digits cannot exceed the defined maximum password length.
Minimum Special Characters Minimum number of special characters in password (!@#$%^&*()_+-={}|[]\;':"<>?,./).
Note: By default, back tick (`), tilde (~), and a leading or trailing space character ( ) are not allowed in a password.
0 -
Minimum Setting: 0
-
Maximum Setting: 64
Note: The number of minimum special characters cannot exceed the defined maximum password length.
Exclude Characters Enter characters to exclude from password.
Note: By default, back tick (`), tilde (~), and a leading or trailing space character ( ) are not allowed in a password.
back tick (`), tilde (~), and a leading or trailing space character ( ) This login rule configuration setting is not currently available.
Maximum Repeat Characters Maximum number of repeated, sequential characters allowed in password.
63 This login rule configuration setting is not currently available..
Min Days Until Password Change Sets the minimum days before a password can be changed.
0 This login rule configuration setting is not currently available.
Max Days Until Password Change Sets the maximum days before a password must be changed.
0 This login rule configuration setting is not currently available.
Failed Login Attempts Number of invalid login attempts until the library locks the user account for the defined number of lockout minutes.
5 This login rule configuration setting is not currently available.
Exclude Previous Passwords Number of new passwords that must be used before a previously used password can be used again.
1 This login rule configuration setting is not currently available.
Max Username Sequence Characters Allowed character sequence from login name allowed in the password.
For example, a login user name is sampleuser and the password rules are set to allow a maximum of a 3 character sequence from the login name to be used in the password.
A password of passworduse123 would be allowed because it meets the criteria for a maximum of a 3 character sequence (use) from the login name in the password.
A password of passworduser123 would not be allow because it contains a 4 character sequence (user) from the login name.
64 This login rule configuration setting is not currently available.
Lockout Minutes Number of minutes before a locked out user can attempt to log into the library.
5 This login rule configuration setting is not currently available.
-
-
Click Apply to save your settings.
-
Click Close to exit the window.
Additional Information
-
In the event that a current password does not meet the current applied login rules, a change password prompt will occur when the user attempts to log in to the WebGUI. The user will then be required to change the password to meet the login rules.
-
LUI logins will not require a password change if the applied login rules change.
Actions
Administrators can use this window to end a user session.
- From the Navigation panel, select User Access.
- In the North Panel, click the checkbox next to the user whose library session you want to end.
- In the Operations panel, click End Session.
- Click Apply to save your settings. The user's session is ended. In the North Panel, the Session column shows a zero (0) indicating the session has ended.