Security
The Security page allows you to configure security settings for the DXi4800, including account management, LDAP/AD, SSL settings, and the inactivity timeout.
To access the Security page, click on Configuration > System > Security.
The Security page contains the following tabs:
The Manage System Users page allows Administrators to manage access to the DXi for the remote management console (GUI) and the command line interface (CLI) pre-configured accounts.
Note: Click on the Show Password icon (![]() ) to see the password. For most password entries, after saving entries and leaving the screen , this icon will no longer show the password.
) to see the password. For most password entries, after saving entries and leaving the screen , this icon will no longer show the password.
The DXi4800 has the following access levels for logging onto the remote management console or the GUI:
| Local Access Level | Description |
|---|---|
| Graphical User Interface (GUI) | |
| GUI Administrator | Allowed to view and change information on the DXi4800 remote management console. |
| GUI Monitor |
Allowed to view information on the DXi4800 remote management console but cannot make changes. The Manage System Users page is view only. |
| GUI Service |
Allowed to view and change information on the DXi4800 GUI. The Manage System Users page is view only. Note: This access level should only be enabled if requested by Quantum Service. |
| Command Line Interface (CLI) | |
| CLI Administrator (username: cliadmin) | Allowed to view and change information on the DXi4800 CLI. |
| CLI Viewer (username: cliviewer) | Allowed to view information on the DXi4800 CLI but cannot make changes. |
| Service Login | |
| SSH/CLI Service (username: ServiceLogin) | Allow Secure Shell (SSH) remote access to the ServiceLogin account. |
To access the Manage System Users page, from the Security tab, click the System Users tab.

Tasks
Use the Manage System Users page to perform the following tasks:
Note: For better security, do not enable these accounts unless they are needed and then disable them when possible.
- Change the administrator password. See Changing the GUI Administrator Password.
- Enable or disable GUI access for the monitor account. See Enabling the GUI Monitor Account.
- Enable or disable CLI access for the administrator or viewer account. See Enabling CLI Accounts.
- Enable or disable GUI access for the service account. See Enabling the GUI Service Account.
- Enable or disable SSH access for the service account. See Enabling the SSH/CLI Service Account.
- Enable or disable IPMI access for the service account. See Security.
Use the GUI password when logging onto the remote management console as an administrator. See Accessing Remote Management.
-
Under GUI Administrator enter the following information:
Old Password Enter the old password. New Password Enter the new password. Confirm New Password Enter the new password again to confirm it. Additional Information
- Disabling the GUI Administrator Account - You cannot disable this account unless LDAP/AD is enabled. In addition, you must also be logged in to the system as an LDAP/AD user. See LDAP/AD. You can, however, disable this account if you have created an RBAC Admin account.
- Passwords can be up to 32 characters. Alphanumeric characters and special characters are allowed.
- Loss of this password will require Quantum service support.
- Click Apply.
Use the GUI password when logging onto the remote management console as a monitor. See Accessing Remote Management.
-
Under GUI Monitor do one of the following steps:
- Select the Enable account check box to enable the GUI monitor account.
- Clear the Enable account check box to disable the GUI monitor account.
-
Enter the following information:
New Password Enter the new password.
Confirm New Password Enter the new password again to confirm it. Additional Information
Passwords can be up to 32 characters. Alphanumeric characters and special characters are allowed.
- Click Apply.
The CLI accounts provide access to the DXi4800 command line interface as an administrator or viewer.
Note: For more information about using the CLI, see the DXi4800 Command Line Interface (CLI) Guide.
-
Under CLI Administrator or CLI Viewer, do one of the following steps:
- Select the Enable account check box to enable the CLI administrator or viewer account.
- Clear the Enable account check box to disable the CLI administrator or viewer account.
-
The CLI administrator and view accounts may be configured with Secure Shell (SSH) key-based authentication.
 Add an SSH Public Key
Add an SSH Public Key
-
Click Add.
The Add Public Key page displays.

-
Enter an SSH Alias for the public key.
Additional Information
- An alias can be up to 20 characters.
- The Alias must be an alphanumeric string (no spaces or special characters).
- The same alias can be used for different accounts (CLI Administrator and CLI Viewer).
-
Copy and paste the Public Key generated from a SSH key.
Additional Information
- A public key should be in the following form: <key-type> <base64 encoded string>.
- A public key length can be up to 16kb.
-
Click Apply.
The "Successfully performed Security action" message appears.
-
Click OK.
The new key appears in the CLI Administrator or View Available SSH Public Keys table.

The Available SSH Public Keys table contains the following information:
Alias Name of key. Fingerprint Short sequence of bytes used to identify a public key.
Sample Public Key Page

 Edit an SSH Public Key
Edit an SSH Public Key
- Select the check box next to the public key in the Available SSH Public Keys table.
-
Click Edit.
The Edit Public Key page displays.

-
Edit the Alias name.
Note: The key cannot be modified. To remove a key, see Delete an Alias Name.
-
Click Apply.
The "Successfully performed Security action" message appears.
-
Click OK.
The updated key appears in the Available SSH Public Keys table.
 Delete an Alias Name
Delete an Alias Name
- Select the check box next to the public key in the Available SSH Public Keys table.
-
Click Delete.
The Delete Public Key page displays.

-
Click Yes.
The "Successfully performed Security action" message appears.
-
Click OK.
The key is removed in the Available SSH Public Keys table.
-
-
In addition to configuring SSH authentication, the CLI Administrator and view accounts may also be configured with password authentication.
- Select the Allow login with password check box to enable a password on a CLI Administrator or CLI Viewer account
- Clear the Allow login with password check box to disable a password on a CLI Administrator or CLI Viewer account
Enter the following information:
New Password Enter the new password. Confirm New Password Enter the new password again to confirm it. Additional Information
- Passwords can be up to 32 characters. Alphanumeric characters and special characters are allowed.
- For accounts enabled with both SSH and password authentication, the DXi system will first attempt SSH authentication . If there are no keys defined or no client key matches, the DXi system will fall back to password authentication.
- Click Apply.
Use the GUI password when logging onto the remote management console as a service account. See Accessing Remote Management.
To enable or disable the GUI service account:
-
Under GUI Service do one of the following steps:
- Select the Enable account check box to enable the GUI service account.
- Clear the Enable account check box to disable the GUI service account.
-
Enter the following information:
New Password Enter the new password. Confirm New Password Enter the new password again to confirm it. Additional Information
Passwords can be up to 32 characters. Alphanumeric characters and special characters are allowed.
- Click Apply.
The SSH service account provides SSH remote access to the DXi4800 system.
-
Under SSH Service, do one of the following steps:
- Select the Enable account check box to enable SSH service account
- Clear the Enable account check box to disable the SSH service account
-
The SSH service account may be configured with Secure Shell (SSH) key-based authentication.
 Add an SSH Public Key
Add an SSH Public Key
-
Click Add.
The Add Public Key page displays.

-
Enter an SSH Alias for the public key.
Additional Information
- An alias can be up to 20 characters.
- The Alias must be an alphanumeric string (no spaces or special characters).
-
Enter the Public Key generated from a SSH key.
Additional Information
- A public key should be in the following form: <key-type> <base64 encoded string>.
- A public key length can be up to 16kb.
-
Click Apply.
The "Successfully performed Security action" message appears.
-
Click OK.
The new key appears in the Available SSH Public Keys table.

The Available SSH Public Keys table contains the following information:
Alias Name of key. Fingerprint Short sequence of bytes used to identify a public key.
Sample Public Key Page

 Edit an SSH Public Key
Edit an SSH Public Key
- Select the check box next to the public key in the Available SSH Public Keys table.
-
Click Edit.
The Edit Public Key page displays.

-
Edit the Alias name.
Note: The key cannot be modified. To remove a key, see Delete an Alias Name.
-
Click Apply.
The "Successfully performed Security action" message appears.
-
Click OK.
The updated key appears in the Available SSH Public Keys table.
 Delete an Alias Name
Delete an Alias Name
- Select the check box next to the public key in the Available SSH Public Keys table.
-
Click Delete.
The Delete Public Key page displays.

-
Click Yes.
The "Successfully performed Security action" message appears.
-
Click OK.
The key is removed from the Available SSH Public Keys table.
-
-
In addition to configuring SSH authentication, the SSH service account may also be configured with password authentication.
- Select the Allow login with password check box to enable a password on a CLI administrator or CLI viewer account.
- Clear the Allow login with password check box to disable a password on a CLI administrator or CLI viewer account.
Enter the following information:
New Password Enter the new password. Confirm New Password Enter the new password again to confirm it. Additional Information
- Passwords can be up to 20 characters. Alphanumeric characters and special characters are allowed.
- For accounts enabled with both SSH and password authentication, the system will first attempt SSH authentication . If there are no keys defined or no client key matches, the system will fall back to password authentication.
- Click Apply.
The Users page allows DXi4800 System Administrators to:
-
Add new users for accessing the DXi4800 via the remote management console (GUI) and the command line interface (CLI). Specify the users' roles as Administrator or Operator, which will define users' access to the DXi4800 (GUI and CLI).
-
Create groups with access rights to specific storage servers, shares, and partitions. Assign the users with Administrator and Operator roles to the new groups, to define their access within the system.
Note: Assigning Administrators to groups is recommended for group organization but is not required, as Administrators have rights to view and modify all storage server data, shares, and partitions.
Caution: When you use this page to enable Operators access to specific storage servers, shares, and partitions, your screen views and access to several different screens and tabs in the DXi4800 GUI, and many links available to Administrators will become unavailable. For example, when Operators click on the Map menu option, they will see only the screens in the system where they have access. See the Management Pages section in The Remote Management Console for an interactive map showing not only available screens based on your access rights but clickable links to reach those pages.
To access the Users page, from the Security tab, click the Users tab. Use the Filter box in either the Users or Groups section to dynamically filter those lists' names.

Note: To sort list contents, click on the up or down arrow next to any column heading. The list sorts to display alphabetically, in either ascending or descending order.
Tasks
Use the Users page to perform the following tasks:
- Add users in the DXi4800 system, with assigned roles as either Administrators or Operators. See Adding Users and Assigning Roles.
- Edit an existing user's credentials. See Editing Users.
- Delete an existing user. See Deleting Users.
- Create a group, adding users and specifying access to specific shares and partitions. See Adding a Group.
- Edit an existing group's name, descriptions, modify assigned users and the group's access to specific storage servers, shares, and partitions. See Editing a Group.
- Delete an existing group. See Deleting a Group.
To add a User and assign credentials and a role:
-
On the Users screen under Users, click Add.
-
In the Name box type the name for the new user.
Note: A User and a Group cannot have the same name.
Note: Maximum length for the Name field is 31 characters. Valid characters are A-Z, a-z, 0-9, -, _, and . Dashes are not allowed at the beginning of the username. Fully numeric usernames and usernames . or .. are also not allowed.
-
Click to assign the Role for the new user, either:
-
Operator - The user will have access to specific storage servers, shares or partitions based on the Group(s) to which the user belongs. Operators are also limited in access to some GUI and CLI commands.
-
Administrator - Users who are designated as Administrators will have access to all storage servers, shares and partitions. Administrators have full access to all GUI and CLI commands.
-
In the Password box type the new user's password.
-
In the Confirm Password box retype the password.
-
The two passwords must be identical.
-
You cannot copy-and-paste the new password from the Password box into the Confirm Password box. It must be retyped.
-
(Optional) In the Description box type a description of the user. This can include the planned group(s) for access, department or working function for the user, assigned shares, etc. The Description can be up to 255 characters.
-
Click Apply to add the new user in the system.
The new user is displayed in the Users list.
Note: To sort the list alphabetically by Users' names or Roles, click on the Name or Role column headings. The list sorts to display alphabetically.
The Add User screen is displayed.

Note: User roles cannot be changed using the Edit User dialog. To change a user from Operator to Administrator or Administrator to Operator, you must delete the user and re-add with the new role.
IMPORTANT
Passwords must be between 8-64 characters, and must include at least one upper case (A-Z), one lowercase (a-z), one number (0-9), and one special character ( ` ~ ! @ # $ % ^ & * ( ) - _ = + [ ] { } \ | ; : ' " , . < > / ? space ).
Note: Existing passwords for all users remain valid and are not subject to these requirements.
To edit an existing User's assigned credentials:
-
On the Users screen under Users, click in the row for the user to edit and click Edit.
-
In the Name box edit or change the User's name.
Note: A User and a Group cannot have the same name.
Note: Maximum length for the Name field is 31 characters. Valid characters are A-Z, a-z, 0-9, -, _, and . Dashes are not allowed at the beginning of the username. Fully numeric usernames and usernames . or .. are also not allowed.
-
In the Password box edit or change the user's password.
-
In the Confirm Password box retype the password.
-
The two passwords must be identical.
-
You cannot copy-and-paste the new password from the Password box into the Confirm Password box. It must be retyped.
-
(Optional) in the Description box edit or change the description of the user. This can include the planned group(s) for access, department or working function for the user.
-
Click Apply to save the user changes in the system.
The Edit User dialog is displayed.

Note: All fields on this screen are optional. The user's Role cannot be changed on this screen. To change the role, delete the User and add them in the new role. Only one user at a time can be edited. See Deleting Users and Adding Users and Assigning Roles.
IMPORTANT
To delete an existing User from the system:
-
On the Users screen under Users, click in the row for the user to delete and click Delete.
-
Click Yes to delete the user.
A confirmation message appears.
Adding a Group from the Users screen allows you to create a new group, select an unlimited amount of users from the Selectable Users list, and set their rights to view and work in specific storage servers, shares and partitions.
To create a new group and add users from the Selectable Users list:
-
On the Users screen under Groups, click Add.
-
In the Name box type a name for the group.
Note: A Group and a User cannot have the same name.
Note: Maximum length for the Name field is 31 characters. Valid characters are A-Z, a-z, 0-9, -, _, and . Dashes are not allowed at the beginning of the username. Fully numeric usernames and usernames . or .. are also not allowed.
-
(Optional) In the Description box type a description of the group. You can note the planned users' data, share, or partition access, department(s) for the group or any other information.
-
To add Users to the new group, click on the User's name in the list of Selectable Users.
The user moves to the Selected Users list.
Note: To search for a user in the list, either scroll in the alphabetized list to find the name or begin typing the name in the Selectable Users box above the list. As you type the name, the list changes to show applicable user names.
-
Repeat the process for additional users to add to the Selected Users list.
The Add Group dialog is displayed.

To specify group members' access to specific storage servers, shares and partitions:
-
Click on the Storage Servers, Shares, or Partitions tab as applicable to find the items where the group will have assigned access.
-
Click in the box in the row to select each item where the Group will have access.
-
Click Apply to create the Group in the system.
The new Group is displayed in the Groups list.
Use the Edit Group dialog from the Users screen to modify an existing group's:
-
Name
-
Description
-
Assigned Users
-
Specific access to storage servers, shares and partitions.
To modify an existing group's name, description and selected users:
-
On the Users screen under Groups, select the row for the group to edit and click Edit.
-
In the Name box edit or change the group name.
Note: A Group and a User cannot have the same name.
Note: Maximum length for the Name field is 31 characters. Valid characters are A-Z, a-z, 0-9, -, _, and . Dashes are not allowed at the beginning of the username. Fully numeric usernames and usernames . or .. are also not allowed.
-
(Optional) In the Description box edit or type a description of the group. You can note the planned users' data, share, or partition access, department(s) for the group or any other information.
-
To add users to the group, click on the User's name in the list of Selectable Users.
The user's name moves to the Selected Users list.
Note: To search for a user in the list, you can either scroll in the alphabetized list to find the name or type the name in the search box above the list. As you type the name, the list changes to show applicable User names, making it easy to find the desired User.
-
Repeat the process for additional users to add to the Selected Users list.
-
To remove Users from the group, click on the User's name in the list of Selected Users.
The user's name moves to the Selectable Users list.
-
Repeat the process for additional users to remove from the Selected Users list.
The Edit Group dialog is displayed.

To modify the Group members' access to specific storage servers, shares and partitions:
-
Click on the Storage Servers, Shares, or Partitions tab as applicable to find the items where the group will have assigned access.
-
Click in the checked box in each row to select the items where the Group will no longer have access.
-
Click Apply to save your changes to the group.
Note: To search for an item in the list for each tab, you can either scroll in the alphabetized list to find the item or type the name in the search box above the list. As you type the name, the list changes to show applicable items.
The modified Group is displayed in the Groups list.
To delete an existing Group, which removes the group members' access to specified storage servers, shares and partitions:
-
On the Users screen under Groups, click in the row for the group to delete and click Delete.
-
Click Yes to delete the group in the system.
A confirmation message appears.
The LDAP/AD page is used to configure the DXi4800 system to use the LDAPv3 protocol and connect to a remote server for the purpose of authenticating login credentials. The DXi4800 will assign permissions to the login based on the group membership in the LDAP server. Microsoft Active Directory (AD) can be configured to support LDAP and the DXi4800 can then connect to the AD server for the purposes of authenticating login credentials.

LDAP and AD Terms
Common Name (CN)
An attribute that is commonly used to distinguish items at the same (usually top) level in the LDAP hierarchy.
Example
The SysAdmin group would have cn=sysadmin.
Domain Component (DC)
The domain of the directory, which often identifies the organization or company.
Example
Mycompany.com would have a domain of dc=mycompany,dc=com.
Distinguished Name (DN)
A pathway that tells LDAP where information is stored in its directory. LDAP reads the pathway from right to left, with the farthest right components providing the domain of the directory and the farthest left component providing the information for which LDAP is looking.
Organizational Unit (OU)
A component used to organize information into a hierarchical structure. OUs can be used at multiple levels within the LDAP or AD directory, such as to act as a larger Group bucket that then holds individual group OUs.
Tasks
Use the LDAP/AD page to perform the following tasks:
- Enable LDAP/AD. See Enable LDAP/AD.
- Disable LDAP/AD. See Disable LDAP/AD .
- Test LDAP/AD settings. See Test LDAP/AD Settings.
- Test LDAP/AD users. See Test LDAP/AD User.
- Select the Enable LDAP/AD check box to enable the Connection Settings and Search Strings tables.
-
Enter the following Connection Settings information:
Primary Server Enter the LDAP/AD domain server.
Local LDAP Cache
-
The cache will be purged anytime LDAP settings are changed.
-
If LDAP is enabled, the cache can be purged at any time by clicking the Apply button. The cache is purged only if the settings are valid (the LDAP server must be accessible) and saved successfully.
- If the new LDAP domain server is invalid, user credentials from the previous LDAP server will continue to authenticate from the server cache.
Alternate Server (Optional) Enter an alternate LDAP/AD domain server StartTLS/LDAPS Select one of the following:
- Start TLS - Select to encrypt the connections to the LDAP/AD server. This enables a secure connection over a standard port. Do not enable Start TLS to encrypt connections if the server URL uses a secure protocol (LDAPS).
- LDAPS - Select if the server URL uses the LDAPS secure protocol.
Port - Start TLS - Default port is 389.
- LDAPS - Default port is 636.
Note: Entering a port setting will disable the default port settings.
Schema Specifies the Schema Type in use on the target LDAP server.
IMPORTANT NOTES:
-
Selecting OpenLDAP will set ldap_schema to rfc2307bis and will require the
memberOfattribute. -
OpenLDAP servers require the
Slapo-MemberOfoverlay to be installed on the server. Refer to http://manpages.courier-mta.org/htmlman5/slapo-memberof.5.html for more information on the overlay.
Select one of the following:
-
OpenLDAP
-
Active Directory
-
IPA
Options Case Sensitive - Select this box to indicate user names are case sensitive. The box is checked by default for OpenLDAP and IPA schemas. The box is unchecked by default for the Active Directory schema. The state of the box can be changed to override the default behavior. Check with an administrator of the LDAP server for the correct value.
Test Password Expiration - This check box is available only when schema IPA is specified. The IPA server may allow an expired account to be authenticated. Select this box to perform a test, in addition to authentication, for expiration of the account.
Password Expiration Attribute This field is available only when Test Password Expiration is checked. This is the name of the attribute that will checked for the expiration date/time information. The default value is
krbPasswordExpiration.Certificate URL Enter the URL where the Certificate Authority (CA) certificate in PEM format can be downloaded.
Note: As only the Certificate URL or the Certificate File can be used to upload a certificate, entries in the Certificate URL field will automatically gray-out (make inactive) the Certificate File field.
CA Certificate Expiration Alerts
The following system alerts occur as a certificate approaches expiration:
- 14 days from expiration - An admin alert is created. See Admin Alerts.
- 3 days from expiration - If the local GUI Admin account is enabled, an admin alert is created. If the local GUI Admin account is disabled, a service ticket is created. See Admin Alerts and Service Tickets.
- 1 day from expiration - If the local GUI Admin account is enabled, an admin alert is created. If the local GUI Admin account is disabled, the account is enabled and a service ticket is created. See Admin Alerts and Service Tickets.
Certificate File Click Browse to browse to and select the local file to upload to the system.
Note: As only one or the other can be used to upload a certificate, entries in the Certificate File field will automatically gray-out (make inactive) the Certificate URL field.
Principal (bind) DN Enter the domain name of the principal user. The principal is an account on the LDAP server that can access the authentication hierarchy.
Example - uid=admin,ou=People,dc=mycompany,dc=comPassword Enter the password for the principal user. Confirm Password Re-enter the password for the principal user. -
-
Enter the following Search Strings information:
User DN Enter a distinguished name for retrieving user information.
Example - dc=mycompany,dc=comMonitor Group Enter a distinguished name or common name for the monitor users allowed on the system. One group (Monitor or Admin) is required for LDAP/AD configuration.
Example - cn=user,ou=Group,dc=mycompany,dc=comAdmin Group Enter a distinguished name or common name for the admin users allowed on the system. One group (Monitor or Admin) is required for LDAP/AD configuration.
Example - cn=sysadmin,ou=Group,dc=mycompany,dc=comAccess Control Administrator Group Enter a distinguished name or common name for the group that will contain access control administrators. Any members of the group that require access to the DXi4800must also be added as users on the DXi4800. See Adding Users and Assigning Roles. Access Control Operator Group Enter a distinguished name or common name for the group that will contain access control operators. Any members of the group that require access to the DXi4800 must also be added as users on the DXi4800. See Adding Users and Assigning Roles. -
(Recommended) Test the LDAP/AD settings before applying the settings to the DXi4800 system. See Test LDAP/AD Settings.
- (Recommended) Test LDAP/AD usernames and passwords before applying the LDAP/AD settings to the DXi4800 system. See Test LDAP/AD User.
-
Click Apply. Changes to LDAP/AD settings force a log out of the DXi4800 system. Click Yes on the confirmation dialog to continue.
Note: Clicking the Apply button will purge the LDAP/AD cache of authenticated accounts if the settings are valid.

Passwords must be between 8-64 characters, and must include at least one upper case (A-Z), one lowercase (a-z), one number (0-9), and one special character ( ` ~ ! @ # $ % ^ & * ( ) - _ = + [ ] { } \ | ; : ' " , . < > / ? space ).
Note: Existing passwords for all users remain valid and are not subject to these requirements.
De-select the Enable LDAP/AD check box to disable LDAP/AD on the DXi4800 system. The LDAP/AD settings remain saved.
Click Test Settings to test the connection settings between the DXi4800 system and LDAP/AD domain server. A successful connection will be indicated by a Success dialog box. A test connection that fails will be indicated by a Failure dialog box containing the reason for the failure.
Successful LDAP/AD Connection

Failed LDAP/AD Connection

Note: User LDAP/AD setting changes must first be applied before being tested.
-
Click Test User to test the ability of a LDAP/AD user to successfully log into the DXi4800 system. The Test Username and Search Strings dialog box opens.

-
Enter the following information:
Username Enter the user name. Password Enter the user password. - Click Test.
The SSL/TLS page allows you to enable or disable SSL/TLS on the DXi4800. You can also install a new SSL certificate to replace the Quantum default SSL/TLS certificate.
To access the SSL/TLS page, on the Security page, click the SSL/TLS tab.

Additional Information
-
If you enable SSL/TLS see Server Authentication Warnings for important information about Web browser settings.
- SSL/TLS is automatically enabled by default after a fresh installation of DXi software.
Tasks
Use the SSL/TLS page to perform the following tasks:
- Enable or disable SSL/TLS on the DXi4800. See Enabling SSL/TLS.
- Install a new SSL/TLS certificate. See Installing an SSL/TLS Certificate.
SSL (Secure Sockets Layer)/TLS (Transport Layer Security) is a protocol that provides security and privacy over the Internet by negotiating encryption keys before transmitting data between a client and a server.
To establish a secure connection, the DXi4800 must have an encryption key assigned to it by a Certification Authority in the form of a certificate file, private key file, and pass phrase. After you install these components, you can establish a secure connection using the SSL/TLS protocol. The DXi4800 comes with a Quantum default SSL/TLS certificate.
To enable or disable SSL/TLS:
- Under SSL/TLS Properties, select the Enable SSL/TLS option to enable SSL/TLS.
- Click Apply.
Or select the Disable SSL/TLS option to disable SSL/TLS.
Note: The default setting is disabled.
Enabling SSL/TLS with the default Quantum certificate allows you to securely communicate with the DXi4800 Web-based interface using SSL/TLS encryption. However, you may receive a warning from your Web browser and network security scanners stating that the server you are attempting to connect to does not match the server embedded within the certificate.
This is expected behavior because the default certificate can only be used for encryption and not server authentication. Quantum recommends the default Quantum certificate be replaced with your own official certificate specific to your DXi system. You can install your own custom certificate in order to take advantage of server authentication in addition to encrypted communication.
Suppress the server authentication warnings as you would for any site based on the browser you are using.
Caution: Quantum recommends that you ALWAYS confirm the correct URL before supressing server authentication warnings.
You can purchase and install your own custom SSL/TLS certificate in order to take advantage of server authentication in addition to encrypted communication on the DXi4800.
To install an SSL/TLS certificate:
-
Under Certificate, click New.
The Install New Certificate page displays.

-
In the Certificate File box, type the location and filename of the new SSL/TLS certificate file.
Or click Browse to browse the system and locate the SSL/TLS certificate file. The SSL/TLS certificate file must be named server.crt.
- Click Upload.
- Type your SSL/TLS private key and press Enter.
-
Type your SSL/TLS passphrase and press Enter.
A Successful Upload page displays stating that the SSL/TLS certificate file has been installed on the system.
-
Click OK.
The certificate displays in the Certificate section.
The Data Encryption page allows you to select the type of encryption to use for Replication, OST, and Accent data transfers. Data sent from the media server (OST/Accent) or source DXi (Replication) to the DXi can be encrypted using AES (Advanced Encryption Standard) encryption methods.
To access the Data Encryption page, on the Security page, click the Data Encryption tab.
Important Information
-
If TLS with AES 256 is selected, the factory installed certificates are inadequate for security. The factory installed certificates should be considered public domain and are provided only for convenience. You must install new certificates for secure encryption.
- The DXi uses the TLS with AES 256 certificate authority as the arbiter of trust. To ensure the security of your data on the DXi blockpool, you must generate your own private certificate authority.
-
Certificates must contain the following key usage fields / extensions, (replace <<URI>> with the applicable URI)
basicConstraints = CA:FALSE
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer:always
keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment, keyAgreement
extendedKeyUsage = critical, serverAuth, clientAuth
crlDistributionPoints = URI:<<URI>>
subjectAltName=${ENV::BC_SAN}
- Installing new certificates requires a reboot of the system.

How to: Certificate Generation Using a Certification Authority (CA)
Step 1: Generate Private Key
Generate a private key to be used for creating the Certificate Signing Request (CSR):
$ openssl genrsa -out key.pem 2048
Step 2: Generate Certificate Signing Request (CSR)
Generate a CSR using the private key. Ensure that the Common Name (CN) in the CSR matches the hostname of your server.
$ openssl req -new -key key.pem -out csr.pem -subj "/C=IN/ST=KA/L=bangalore/O=quantum/CN=server-1/emailAddress=test@quantum.com"
Note: The CSR includes the public key and information such as the server's hostname, organization, and country.
Note: Verify that the CN field corresponds to the hostname of the server.
Step 3: Submit CSR to the Certificate Authority (CA)
Provide the generated csr.pem file to your Certificate Authority for signing. The CA will issue a signed certificate (e.g., cert.pem) and may also provide intermediate certificates.
Full Certificate Chain Requirement:
-
The ROOT CA need to be combined with all intermediate certificates provided by the CA into a full certificate chain.
-
Example of a chained CA certificate file (cacert.pem):
-----BEGIN CERTIFICATE-----
ROOT CA cert
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
SUB CA cert
-----END CERTIFICATE-----
Note: The order of certificates in the chain can sometimes affect the validation process. Ensure the Root CA is at the top, followed by intermediate CAs in hierarchical order.
Step 4: Validate the Signed Certificate
Once you receive the signed certificate (cert.pem), verify it against the full CA certificate chain:
$ openssl verify -CAfile cacert.pem cert.pem
cert.pem: OK
Note: If validation fails, check that the full certificate chain is correct and in the appropriate order.
Step 5: Deploy the Certificates
Upload the following files to the server in TLS Certificates section:
1. Certificate File (Signed Certificate - cert.pem)
2. Private Key File (key.pem)
3. Certificate Authority File (Full Certificate Chain - cacert.pem)
Additional Notes:
Order of Certificates in cacert.pem:
-
The order can matter in some implementations. Ensure the Root CA is first, followed by intermediate CAs in order of hierarchy.
-
If validation fails, try reordering the certificates in cacert.pem and test again.
Common Errors:
-
Validation may fail if the full chain is incomplete
To enable or disable data encryption:
-
Select an Encryption option in OST and Accent Data Transfer Encryption:
None Data is not encrypted. Default AES 128 OST and Accent data is encrypted using AES 128-bit encryption. Default AES 256 OST and Accent is encrypted using AES 256-bit encryption. TLS with AES 256 OST, Accent, and Replication data is encrypted using AES 256-bit encryption with Transport Layer Security (TLS).
For replication, you must specify encryption settings when configuring the replication or failback targets. See Replication .
-
If you selected the TLS with AES 256 encryption option, install the required TLS Certificate and key files on the DXi4800 system:
- Certificate File
- Private Key File
- Certificate Authority File
- Certificate Revocation List (Optional)
OST Media Server with TLS Encryption
The certificate and key files installed on the DXi4800 system must match the files on the OST media server. For more information on certificate and key files, see the OST Plug-in Installation Instructions.
Replication with TLS Encryption
To successfully use replication with TLS encryption, you must do the following:
- Configure target DXi4800 with TLS Encryption.
- Configure source DXi4800 with TLS Encryption (system reboot required).
- Select TLS with AES 256 when configuring the target DXi4800. See Adding a Replication Target.
The source DXi4800 key and target DXi4800 key do not need to match, but must meet the following criteria:
- The target key must be signed by a certificate in the source key.
- The source key must be signed by a certificate in the target key.
To install a file, click the Browse button to browse the system and locate the file, and then click Open.
Caution: Installing certificate files requires a system reboot immediately after the changes are applied. Wait for at least 15 minutes before logging back in.
Note: You can install new certificate and key files at any time, as long as there are no active network connections between the server and the DXi4800.
-
Click Apply. Changes made to the TLS Certificates will require a system reboot and the Save Changes dialog box appears.

Select one of the following options.
Option Description Defer Reboot Defers the system reboot. A Reboot Required alert message will appear in the GUI banner until the system is rebooted.
Deferring a reboot is only recommended if additional system changes that require a reboot need to be made (Network, Application Environment, Data Encryption changes) or ingest (backup jobs) are currently in progress on the system.
Note: Once a reboot is in a deferred state, the applied changes cannot be reset.
Reboot Now Starts the system reboot. A system reboot can take up to 15 minutes.
Cancel No reboot occurs and the Data Encryption page reappears. Changes made to the settings remain but are not applied. Click Reset to reset settings to their original state. Additional Information
- To revert all network settings to the initial state and undo all changes, click the Reset button.
- To clear all changes without saving them, click Reset. To remove user installed certificate and key files, click Restore Factory Defaults.
The Login Settings page allows Administrators to:
-
Set the system's inactivity timeout in minutes.
-
Enable and disable Multi-Factor Authentication (MFA).
Tasks
Use the controls on the Login Settings page to complete the following tasks:
To access the Login Settings page, on the Security tab, click on the Login Settings tab.

The Inactivity Timeout setting allows you to specify the inactivity timeout for the DXi4800 remote management console. The default timeout is 30 minutes.
When the remote management console is inactive for the time period specified, the user is automatically logged off and must log back on to continue. See Accessing Remote Management.

To specify the inactivity timeout for all system users:
- In the Inactivity Timeout box, enter the number of minutes of inactivity before a user is automatically logged off (1–600 minutes).
- Click Apply.
GUI Administrators use this feature to enable DXi MFA (Multi-Factor Authentication) feature for RBAC (Role-based Access Control) users. See Adding Users and Assigning Roles for instructions on adding RBAC users.
NOTES
-
For systems configured to use the LDAPv3 protocol and connect to a remote server for the purpose of authenticating login credentials, MFA rules apply to those users. See LDAP/AD.
-
SSH/CLI Service users (username: ServiceLogin) are not required to login with MFA credentials.
-
Downloading an authenticator program is the suggested method of working with MFA.
To enable the system to use MFA:
-
Under OTP (One-time Password), check the Enable Multi-Factor Authentication box.

Note: NTP must be enabled to enable the Time-based One-time password and enable MFA. See Date & Time.
-
Click Apply.
All users created on the Users page will need to set up and use MFA. See Set Up Multi-Factor Authentication.
After enabling MFA, when users are added in the system using the System > Security > Users page, at first login, they will need to set up their MFA:
-
At the Login screen, type your Username and Password, and then click on Login.
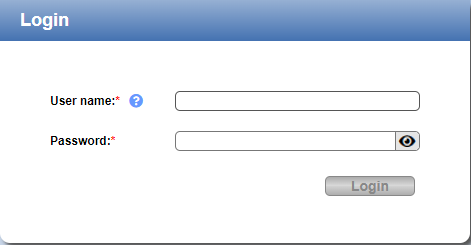
Passwords must be between 8-64 characters, and must include at least one upper case (A-Z), one lowercase (a-z), one number (0-9), and one special character ( ` ~ ! @ # $ % ^ & * ( ) - _ = + [ ] { } \ | ; : ' " , . < > / ? space ).
Note: Existing passwords for all users remain valid and are not subject to these requirements.
-
The Login screen changes to display a QR code screen similar to the following image:

-
Using your authenticator application, select your account for company use and either:
-
Scan the QR code.
-
Copy and paste or type the 32-character Shared Secret Code into your authenticator application.
Your authenticator application generates a 6-digit One-time password code.
-
-
On the Login screen still displaying the QR code, type the One-time password code in the Authentication code box, and then click Apply.
You are logged on to your DXi system with your MFA code and the Home screen is displayed.
For subsequent logins after completing your MFA setup:
-
At the Login screen, type your Username and Password, and then click on Login.

The Login screen changes to display an Authentication code box.
-
Using your Microsoft Authenticator application, select your company account and type the 6-digit One-time password code in the DXi Login screen Authentication code box, and then click Apply.

You are logged on to your DXi system with your MFA code and the Home screen is displayed. This is now your regular login process.
Caution: Disabling MFA deletes all secret keys created for RBAC-setup users. When MFA is re-enabled, users will need to re-authenticate using the steps in Set Up Multi-Factor Authentication and Subsequent Logins After MFA Setup.
To disable MFA for all system users:
-
Under OTP (One-time Password), un-check the Enable Multi-Factor Authentication box.

A confirmation message displays, reminding you that disabling MFA for all users and the secret authentication key for each will be deleted from the system.

- Click Yes to continue or No if you need to leave MFA in place for the system.
If, for example, a user loses their phone containing the authenticator application and their account information, the GUI Administrator can delete the user's secret key. Under TOTP User Settings, click in the Username box under Delete user's secret key and enter the user's Username to remove the user's Shared Secret Code from the system.
Note: The terms Secret Key and Shared Secret Code refer to the same character string. The terms will be merged in a future release.

To remove a user's secret key:
-
Under TOTP User Settings, type the user's Username in the Username box.
-
Click on Delete secret key.
A confirmation message is displayed.
-
Click on Yes to confirm the deletion.
Note: A system message on the screen confirms that the user's secret key has been deleted. At the user's next login to DXi , they must repeat the processes in Set Up Multi-Factor Authentication and Subsequent Logins After MFA Setup. They may also need to add their company account in Authenticator.
The Security Notice page allows you to specify a message that will appear to all users when logging on to the remote management console or the CLI (command line interface).
If a security notice message has been specified, the user must accept the message in order to begin using the system. If no security notice has been specified, the user can use the system immediately after logging on.
To access the Security Notice page, on the Security page, click Security Notice.

To add or update a security notice message, enter the message in the box and click Apply.
The Data-at-Rest page allows you to enable Data-at-Rest Encryption on the DXi4800 and manage security keys.
Note: The Data-at-Rest page displays only if the Data-at-Rest Encryption feature is supported on the DXi4800 and is licensed for use
Caution: After you enable Data-at-Rest Encryption, you cannot disable it or turn it off. Make sure to back up your passphrase and recovery files, as they may be required for future capacity expansion or in certain, rare hardware failure scenarios. See Managing Recovery Files.
To access the Data-at-Rest page, on the Security page, click the Data-at-Rest tab.
WARNING: This page takes a few minutes to update.

Tasks
Use the Data-at-Rest page to perform the following tasks:
- Check the current status of Data-at-Rest Encryption. See Checking Data-at-Rest Encryption Status.
- Enable Data-at-Rest Encryption for all hard drives in the DXi4800. See Enabling Data-at-Rest Encryption.
- Save or e-mail a Data-at-Rest Recovery file to back up your encryption keys. See Managing Recovery Files.
The current status of Data-at-Rest Encryption can be Disabled (default) or Enabled. If it is enabled, all drives in the DXi4800 are securely encrypted and cannot be read if removed from the system.
Click Check Status to view detailed information about the status of Data-at-Rest Encryption and to see if the DXi4800 supports all requirements for enabling the feature.
When Data-at-Rest Encryption is enabled, all hard drives in the DXi4800 are paired to their respective RAID controllers using encryption keys. These keys are generated using a passphrase that you supply.
Caution: Make sure you are certain you want to enable Data-at-Rest Encryption before proceeding. After you enable Data-at-Rest Encryption, you cannot disable it or turn it off.
To enable Data-at-Rest Encryption:
-
Verify that the system is in an optimal state:
-
All hardware statuses on the system are Normal. See Hardware.
Caution: All storage arrays must show Normal condition. If any storage arrays are degraded, do not enable Data-at-Rest Encryption. See Details.
- All outstanding administration alerts are deleted. See Admin Alerts.
- All service tickets are closed. See Service Tickets.
-
-
Under Enable Data-at-Rest Encryption, type a security passphrase in the Passphrase box.
Caution: If you are re-enabling Data-at-Rest Encryption, you must enter the same passphrase that was used when encryption was originally enabled.
The passphrase must meet all of the following requirements:
- Must be 8–32 characters long.
- Must contain at least 1 digit [0–9].
- Must contain at least 1 uppercase letter [A–Z].
- Must contain at least 1 lowercase letter [a–z].
-
Must contain at least 1 non-alphanumerical character, for example, ‘+’ or ‘@’.
Note: An underscore [ _ ] is considered an alphanumeric character.
- Must not contain a space, tab, single quote [‘], double quote [“], or dollar sign [$].
- Enter the passphrase again in the Confirm Passphrase box.
- Click Enable.
Data-at-Rest Encryption is now enabled, and all hard drives are secured so that, if they are removed from the DXi4800, they cannot be read using another system or device.
Be sure to record the passphrase in a safe location. You should also save a backup copy of the Data-at-Rest Recovery file. See Managing Recovery Files.
When Data-at-Rest Encryption is enabled, the system generates security keys based on the supplied passphrase. The DXi4800 maintains a copy of the security keys on the system, and they are accessed automatically as needed.
There are a few, rare situations which may require manual entry of the passphrase, such as performing a capacity expansion, or in certain hardware failure scenarios. The Data-at-Rest Recovery file is a password protected .xml file that contains an encryption key identifier and passphrase for the controller. The encryption key identifier provides the system serial number, product ID, and location for the controller.
Sample Data-at-Rest Recovery File
?xml version="1.0" encoding="UTF-8"?>
<xml>
<EncryptionKeyAttributes>
<LastModified>Tue May 08 17:14:29 2018</LastModified>
<SASAddress>500605b00cb96080</SASAddress>
<EncryptionKeyIdentifier>YM6D003111-EP420e-a0</EncryptionKeyIdentifier>
<Passphrase>SamplePassword</Passphrase>
</EncryptionKeyAttributes>
</xml>
To download or send a copy of the recovery file:
-
Under Download/Send Data-at-Rest Recovery File, select an option:
Download Downloads a copy of the recovery file using the Web browser. Email Sends a copy of the recovery file using e-mail. If selecting this option, type the e-mail address where you want to send the recovery file in the Email Recipient box. Note: For the DXi4800 to send an e-mail, you must specify an outgoing e-mail server. See Email.
-
Type a security password in the Password box, and type it again in the Confirm Password box.
This password is used to protect the recovery file. You will be prompted for this password when opening the recovery file.
Passwords must meet all of the following requirements:
-
Must be 8–32 characters long.
-
Must contain at least 1 digit [0–9].
-
Must contain at least 1 uppercase letter [A–Z].
-
Must contain at least 1 lowercase letter [a–z].
-
Must contain at least 1 non-alphanumerical character, for example, ‘+’ or ‘@’.
-
Note: An underscore [ _ ] is considered an alphanumeric character.
- Must not contain a space, tab, single quote [‘], double quote [“], or dollar sign [$].
-
- Click Apply.
For the download option, click OK or Save to save the recovery file. For the email option, the recovery file is automatically sent to the email address you specified.
Keep a copy of the recovery file in a safe location in case it is needed later. The recovery file is a password-protected ZIP format file. To unzip the file, you must enter the password specified in step 2 above. The recovery file contains the passphrase used to enable Data-at-Rest Encryption as well as the security keys.
