Scalar i6000 Encryption
Overview
The library supports several encryption key management solutions. These solutions work in conjunction with the library to generate, protect, store, and manage encryption keys. The keys are used by tape drives to encrypt information being written to, and decrypt information being read from, media. The library communicates with the encryption key management server(s). The encryption keys pass through the library, so that encryption is transparent to the applications. Using the library in this way is known as library managed encryption.
Encryption Key Management (EKM)
The Encryption Key Management (EKM) feature enables support for Library-Managed Encryption (LME) with Scalar Key Manager configurations, or Key Management Interoperability Protocol (KMIP) connected encryption key servers, as well as IBM TKLM/SKLM/GSKLM encryption key management solutions via an IBM Proprietary Protocol (IPP) connection.
- Q-EKM
- TKLM/SKLM
A tape library can only configure a single EKM solution for library manged encryption (LME). Encryption can be enabled or disabled per partition. By default, LME is disabled per partition. However, encryption-capable tape drives are configured for application managed encryption (AME) by default, so that an application is able to request drives to encrypt/decrypt data without the need for any specific library configuration.
Additional Information
-
The library does not support using more than one encryption key management system on a single library
-
Media with unencrypted data on it will remain unencrypted. Media with unencrypted data will not be encrypted until they are erased or relabeled. Erasing and relabeling operations will destroy existing unencrypted data on the media.
WARNING: No changes to the encryption settings can be made while library partitions are configured to use Library-Managed Encryption (LME). LME must first be disabled on the partition before making changes to the encryption settings (see Encryption Key Management (EKM)).
Encryption involves the use of several kinds of keys. How these keys are generated, maintained, controlled, and transmitted depends upon the operating environment where the encrypting tape drive is installed. Some host applications are capable of performing key management. For environments without such applications or those where application agnostic encryption is desired, Quantum provides the Scalar Key Manager (SKM) solution to perform all necessary key management tasks.
Scalar Key Manager - How it Works
Scalar Key Manager (SKM) generates, protects, stores, and maintains data encryption keys that are used to encrypt information being written to, and decrypt information being read from, tape media (tape and cartridge formats).
SKM acts as a process awaiting key generation or key retrieval requests sent to it through a secure TCP/IP communication path between SKM and the tape library.
When a new data encryption key is needed, the tape drive requests a key, which the library forwards to the primary SKM server. The library requests a data encryption key from the primary SKM server first, unless the primary SKM server is down and failover to the secondary SKM server has occurred. If failover to the secondary SKM server occurred, then the library continues to request data encryption keys from the secondary SKM server until either the library is rebooted or the secondary server goes down and failover back to the primary occurs.
After a library reboot, the library goes back to forwarding requests to the primary server.
Upon receipt of the request, SKM retrieves an existing data encryption key from the keystore and securely transfers it to the library, which then provides it to the tape drive where it is used to encrypt the data being written to tape. Once a data encryption key is assigned to a tape, it is never reused on another tape.
When an encrypted tape is read by a tape drive, the tape drive requests, via the library, the required data encryption key from the SKM server. SKM retrieves the required data encryption key from the keystore and securely transfers it to the library, which provides it to the tape drive. The tape drive uses the data encryption key to perform encryption or decryption.
No data encryption key is stored anywhere on the cartridge memory or the tape. Only the name of the data encryption key is stored on the tape, so that in the future the key can be requested for further read or write purposes. The first read/write operation on an encrypted tape requires the tape drive to request the data encryption key.
The Key Management Interoperability Protocol (KMIP) is a specification developed by OASIS. Its function is to standardize communication between enterprise key management systems and encryption systems.
KMIP is only supported in certain environments. Contact your Quantum representative for details.
Details about the KMIP-compliant implementation include:
- As with other encryption systems supported by the library, in order to use KMIP-compliant encryption systems, you must have an Encryption Key Management license installed on the library.
- A minimum of two KMIP-compliant encryption servers is recommended to ensure keys are backed up to alternate servers for safe keeping and disaster recovery.
Q-EKM is an optional, licensed Java software program that generates, protects, stores, and manages the encryption keys. These keys are used by the LTO-4, LTO-5 or LTO-6 tape drives to encrypt the information being written to tape media and read from tape media. Policy control and keys pass through the library-to-drive interface; therefore encryption is transparent. Q-EKM was designed to generate and communicate encryption keys for LTO-4, LTO-5 or LTO-6 drives in Quantum libraries across the customer’s environment.
Note: Q-EKM encryption is not available for LTO-7 drives. Any partitions that contain LTO-7 drives will not be able to encrypt using Q-EKM.
If you choose to purchase and use the licensed Q-EKM application, you must supply a server on which to install EKM. Professional Q-EKM integration must be performed by Quantum or Quantum authorized service personnel. For more information, contact the Quantum Technical Assistance Center at www.quantum.com/support.
Note: Prior to configuring Q-EKM on the Scalar i6000 library, Quantum recommends installing and configuring the Q-EKM server or servers first.
Q-EKM on the Scalar i6000 library supports encrypting LTO-4 or higher tape media using IBM LTO-4 or higher Fibre Channel drives only. All IBM LTO-4, LTO-5 or LTO-6 FC drives are encryption-capable, but to use the Q-EKM software application, you must purchase an Encryption Key Management license and provide a server or servers on which to install Q-EKM. Q-EKM does not currently support encryption on other tape drive types or manufacturer brands, even if they are assigned to a partition selected for encryption.
Note: You must be running Q-EKM version 2.0 (or higher) to support IBM LTO-5 or LTO-6 tape drives.
The encryption keys pass through the library, so that encryption is “transparent” to the applications. If you purchase Q-EKM, Quantum's Service department will schedule an appointment to install the application onto your server(s).
Security Key Lifecycle Manager (SKLM) — formerly Tivoli Key Lifecycle Manager (TKLM) — automates the encryption key management process to help minimize risk and reduce operational costs of key management. It offers secure and robust key storage, key serving and key lifecycle management for IBM and non-IBM storage solutions using the OASIS Key Management Interoperability Protocol (KMIP).
FIPS (Federal Information Processing Standard) 140-2 is a U.S. government standard relating to computer security and encryption.
While encryption key servers are independently FIPS certified, the tape library also supports FIPS 140-2 Level 1 certified encryption solutions with HP LTO-5 and LTO-6 drives, as well as IBM LTO-6, LTO-7 and LTO-8 drives. FIPS mode of operation is configured on a partition-basis and requires the library partition to have only FIPS capable tape drives installed. FIPS capable HP drives are able to enable and disable FIPS mode of operation with any supported tape drive firmware; IBM drives however require FIPS firmware image variant loaded to support enabling of FIPS mode of operation. Once a partition is operating in FIPS mode, all encryption key exchanges are communicated securely via the tape drive's Ethernet interface.
While encryption key servers are independently FIPS certified, the tape library also supports FIPS 140-2 Level 1 certified encryption solutions with IBM LTO-6, LTO-7 and LTO-8 drives. FIPS mode of operation is configured on a partition-basis and requires the library partition to have only FIPS capable tape drives installed. IBM drives require FIPS firmware image variant loaded to support enabling of FIPS mode of operation. Once a partition is operating in FIPS mode, all encryption key exchanges are communicated securely via the tape drive's Ethernet interface.
Additional Information
- An Encryption Key Management license must be installed on the library with an embedded drive count sufficient to cover all tape drives in a partition to enable library-managed encryption.
- FIPS mode of operation can only be enabled if library-managed encryption is enabled for a selected partition.
- FIPS mode of operation requires all drives in the partition to be Ethernet connected.
- FIPS mode of operation supports a mix of LTO drive generations and vendors as long as the drives are FIPS capable.
- FIPS mode is disabled by default.
Caution: If the
If you are running SKM or a KMIP key manager encryption solutions, Transport Layer Security (TLS) communication certificates with valid dates must be installed on the library in order for the library to communicate securely with attached EKM servers. At any time, you may install a new set of TLS certificates to overwrite the existing set. The new TLS certificates must all be valid or the overwrite will not occur and the existing certificates will remain in place.
You can install your own TLS certificates (for SKM), or when installing TLS certificates for KMIP key managers. When providing your own certificates, it is assumed you understand the concepts of PKI and can access the tools or third-party resources needed to generate or obtain certificates.
- If you are using SKM: You must be running SKM 2.4 or higher on your SKM servers in order to install your own TLS certificates. If you install your own TLS certificates on the library, you must also install your own certificates on the SKM servers. Similarly, if you use the Quantum-provided TLS certificates on the SKM servers, you must also use the Quantum-provided TLS certificates on the library.
- If you are using KMIP key managers: Your KMIP server provider will provide TLS communication certificates.
When you upload encryption certificates to the library, you will need to provide the following:
| Encryption System | Certificates Required |
|---|---|
| Q-EKM or TKLM/SKLM |
|
| SKM |
|
| KMIP Key Management |
|
Certificate Format
The certificate files must be in the following format. If any of the following requirements is not met, none of the certificates will be uploaded.
-
Root certificate must be 2048 bits.
-
Root certificate must be in PEM format.
-
Admin and Client certificates must be in pkcs12 (.p12) format, with a separate certificate and private key contained in each. The .p12 format combines the public/private key pair files in .pem file format and password protects access to such .pem certificate files.
-
The Admin and Client certificates must be 1024 bits.
-
The Admin and Client certificates must be signed by the Root certificate.
-
Certificates must have the Organization name (O) set in the Issuer and Subject information.
-
(SKM only) The Admin certificate must have its Organizational Unit name (OU) set as "akm_admin" in its Subject Information.
-
The same Root certificate must be installed on the encryption key servers and the library.
-
All the certificates must have a valid validity period according to the date and time settings on the encryption key server.
-
You cannot update encryption communication certificates if there is a library partition in LME mode
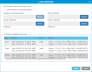
Layout
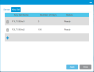
List all available encryption types and any current configuration details.
| Column | Description |
|---|---|
| EKM Solution/ Service IP Address |
Type of encryption: Scalar Key Manager (SKM) KMIP Key Manager, Q-EKM, TKLM/SKLM |
| Configuration Status | Configured or Not Configured. |
| Access Security |
Type of communication security: Native or SSL/TLS. |
| Path Diagnostics | Enabled or Disabled. |
Lists all the configured parameters for any highlighted encryption type.
Shows a summary of the total number of Library- or Application-managed partitions in the library.
Provides options for drive configuration, maintenance and action.
| Configuration | |
|---|---|
| Add | Allows you to define the key management server IP address and port configurations. |
| Modify | Allows you to modify the key management server IP address and port configurations. |
| Delete | Allows you to add, modify, or delete Encryption (EKM) Solutions that are licensed on the library. |
| Actions | |
|---|---|
| Path Diagnostics | Allows you to run series of short tests to validate whether the key servers are running, connected, and able to serve keys as required |
| Load Certificates | Allows you to upload authorized certificates for security on your library. |
Tasks
Configuration
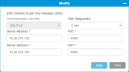
This window allows you to define the key management server IP address and port configurations. You can either add a redundant
- From the Navigation panel, select Encryption.
- In the North Panel, select the check box next to Quantum Encryption Key Manager (Q-EKM).
-
In the Operations panel, click Add.
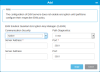
Item Description Action Communication Security Allows you to select from the following values:
- Native
- SSL/TLS
Select a value from the drop-down menu. Server Address Identifies the IP address of the second SKM server. The library will failover to this server if the first SKM server is not available. The library will continue to use this server until it is not available even if the first server become available. Enter text. Path Diagnostics Allows the library to establish a heartbeat with the SKM servers to alert of connectivity or operational failures. Time intervals include:
0 min - no heartbeat path diagnostics are enabled
15 min - path diagnostic heartbeat will be run every 15 minutes
30 min - path diagnostic heartbeat will be run every 30 minutes
60 min - path diagnostic heartbeat will be run every 60 minutes
Select a value from the drop-down menu. Port Identifies SKM port number for first server. Cannot be changed Port Identifies SKM port number for second server. Cannot be changed -
Click Apply to save your settings.
-
Click Close to exit the window.
- From the Navigation panel, select Encryption.
- In the North Panel, select the check box next to IBM Tivoli/Security Key Lifecycle Manager (TKLM/SKLM).
-
In the Operations panel, click Add.
Item Description Action Communication Security Allows you to select from the following values:
- Native
- SSL/TLS
Select a value from the drop-down menu. Server Address Identifies the IP address of the second SKM server. The library will failover to this server if the first SKM server is not available. The library will continue to use this server until it is not available even if the first server become available. Enter text. Path Diagnostics Allows the library to establish a heartbeat with the SKM servers to alert of connectivity or operational failures. Time intervals include:
0 min - no heartbeat path diagnostics are enabled
15 min - path diagnostic heartbeat will be run every 15 minutes
30 min - path diagnostic heartbeat will be run every 30 minutes
60 min - path diagnostic heartbeat will be run every 60 minutes
Select a value from the drop-down menu. Port Identifies SKM port number for first server. Cannot be changed Port Identifies SKM port number for second server. Cannot be changed -
Click Apply to save your settings.
-
Click Close to exit the window.
- From the Navigation panel, select Encryption.
- In the North Panel, select the check box next to Scalar Key Manager (SKM).
-
In the Operations panel, click Add.
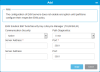
Item Description Action Server Address Identifies the IP address of the first SKM server. The library will contact this server first for all key requests unless it is not available.
Note: It is recommended that you use the geographically closest server in this field.
Enter text. Server Address
Identifies the IP address of the second SKM server. The library will failover to this server if the first SKM server is not available. The library will continue to use this server until it is not available even if the first server become available. Enter text. Path Diagnostics
Allows the library to establish a heartbeat with the SKM servers to alert of connectivity or operational failures. Time intervals include:
0 min - no heartbeat path diagnostics are enabled
15 min - path diagnostic heartbeat will be run every 15 minutes
30 min - path diagnostic heartbeat will be run every 30 minutes
60 min - path diagnostic heartbeat will be run every 60 minutes
Select a value from the drop-down menu. Port Identifies SKM port number for first server. Cannot be changed Port Identifies SKM port number for second server. Cannot be changed -
Click Apply to save your settings.
-
Click Close to exit the window.
- From the Navigation panel, select Encryption.
- In the North Panel, select the check box next to KMIP Key Manager.
-
In the Operations panel, click Add.
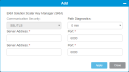
Item Description Action Server Identifies the IP address of the KMIP server. Enter text. Path Diagnostics Allows the library to establish a heartbeat with the SKM servers to alert of connectivity or operational failures. Time intervals include:
0 min - no heartbeat path diagnostics are enabled
15 min - path diagnostic heartbeat will be run every 15 minutes
30 min - path diagnostic heartbeat will be run every 30 minutes
60 min - path diagnostic heartbeat will be run every 60 minutes
Select a value from the drop-down menu. Port Identifies KMIP port number for the servers. Cannot be changed -
Click the + icon to add additional servers.
- Click Apply to save your settings.
- Click Close to exit the window.
This windows allows you to modify the key management server IP address and port configurations. You can either modify your Scalar Key Manager (SKM) solution settings or your Key Management Interoperability Protocol (KMIP) key manager settings.
- From the Navigation panel, select Encryption.
- In the North Panel, select the check box next to Scalar Key Manager (SKM).
-
In the Operations panel, click Modify.
Item Description Action Server Address Identifies the IP address of the first SKM server. The library will contact this server first for all key requests unless it is not available.
Note: It is recommended that you use the geographically closest server in this field.
Enter text. Server Address Identifies the IP address of the second SKM server. The library will failover to this server if the first SKM server is not available. The library will continue to use this server until it is not available even if the first server become available. Enter text. Path Diagnostics Allows the library to establish a heartbeat with the SKM servers to alert of connectivity or operational failures. Time intervals include:
0 min - no heartbeat path diagnostics are enabled
15 min - path diagnostic heartbeat will be run every 15 minutes
30 min - path diagnostic heartbeat will be run every 30 minutes
60 min - path diagnostic heartbeat will be run every 60 minutes
Select a value from the drop-down menu. Port Identifies SKM port number for first server. Cannot be changed. Port Identifies SKM port number for second server. Cannot be changed. -
Click Apply to save your settings.
-
Click Close to exit the window.
- From the Navigation panel, select Encryption.
- In the North Panel, select the check box next to KMIP Key Manager.
-
In the Operations panel, click Modify.
Item Description Action Server Identifies the IP address of the KMIP server. Enter text. Path Diagnostics Allows the library to establish a heartbeat with the SKM servers to alert of connectivity or operational failures. Time intervals include:
0 min - no heartbeat path diagnostics are enabled
15 min - path diagnostic heartbeat will be run every 15 minutes
30 min - path diagnostic heartbeat will be run every 30 minutes
60 min - path diagnostic heartbeat will be run every 60 minutes
Select a value from the drop-down menu. Port Identifies KMIP port number for the servers. Cannot be changed. - Click Apply to save your settings.
-
Click the Key Set tab to modify the key set(s) assigned to the KMIP servers.
Item Description Action Key Set Name Enter key set name.
Enter text. Number of Keys Enter the number of keys in the key set.
Note: You cannot modify the key set number to a number smaller than the original numberl
Enter number. -
Click the + icon to add additional key sets to the KMIP server(s).
- Click Apply to save your settings.
- Click Close to exit the window.
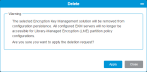
You can add, modify, or delete Encryption (EKM) Solutions that are licensed on the library. To activate the Delete button, you must first have the partition that uses encryption offline and the encryption policy disabled.
Delete all Encryption Settings
To delete all encryption settings under a selected EKM solution, do the following:
- From the Navigation panel, select Encryption.
-
In the North Panel, select the EKM Solution you want to change.
-
In the Operations panel, click Delete.
- Click Apply.
- Click Close to exit the Delete window.
Delete one or more Encryption Server Settings
To delete one or more server settings under a selected EKM solution, do the following:
Actions
The EKM Path Diagnostics consists of a series of short tests to validate whether the key servers are running, connected, and able to serve keys as required.
EKM Diagnostics runs the following tests:
| Ping Test | Verifies the Ethernet communication link between the library and the key servers. |
| Path Test | Verifies that EKM services are running on the key servers. |
| Configuration Test | Verifies that the key servers are capable of serving encryption keys. |
If any of the tests fail, try the following resolutions and run the test again to make sure it passes:
| Ping Test Failure | Verify that the key server host is running and accessible from the network to which the library is connected. |
| Path Test Failure | Verify that the key server is running and that the IP address, port, and SSL settings configured on the library are correct. Check to see if there is a network configuration issue, such as a firewall, preventing communication with the server. |
| Configuration Test Failure |
SKM: A database inconsistency has been detected. Contact Technical Support. KMIP Key Manager: Indicates a KMIP key server configuration problem. The server does not support all features necessary for the library to use it as a key server. Contact your KMIP server administrator for assistance. |
This window is where you will load authorized certificates for security on your library. To add a Quantum certificate bundle you will need to create the bundle using SKM 2.4.
Note: You cannot update encryption communication certificates if there is a library partition in LME mode
Note: Before loading encryption certificates, review the Loading Encryption Certificates - Requirements above.
- From the Navigation panel, select Encryption.
- In the North Panel, select the check box next to either Scalar Key Manager (SKM), KMIP Key Manager, Quantum Encryption Key Manager (Q-EKM), or IBM Tivoli/Security Key Lifecycle Manager (TKLM/SKLM).
-
In the Operations panel, click Load Certificates.
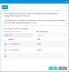
Item Description Action Install Quantum Certificate Bundle Allows you to upload a Quantum specific EKM certificate bundle that includes SKM and KMIP certificates as well as admin, root and client access certificates. Select the checkbox to enable the Quantum Certificate Bundle field. Deselect the checkbox to disable the Quantum Certificate Bundle field. Admin Certificate Allows you to install an administration certificate manually created by you. This field is only available if the Install Quantum Certificate Bundle checkbox is not selected.
Click Browse to navigate to your admin certificate. Root Certificate Allows you to install a root certificate manually created by you. This field is only available if the Install Quantum Certificate Bundle checkbox is not selected. Click Browse to navigate to your admin certificate. Client Certificate Allows you to install a client certificate manually created by you. This field is only available if the Install Quantum Certificate Bundle checkbox is not selected.
Click Browse to navigate to your admin certificate. Password Allows you to enter the password associated with the root certificate. Enter text. Certificate Installation Summary Lists all currently loaded and active certificates for your library.
-
Click Apply to save your settings.
-
Click Close to exit the window.