ActiveScale IAM API
1.0 IAM Overview
Quantum ActiveScale's Identity and Access Management (IAM) provides fine-grained, policy-based access control for S3 resources, replacing the legacy ACL system. The IAM API enables users to define and manage permissions using JSON-based policies, and also control who can assign those permissions. This guide outlines the supported IAM features, setup instructions, policy implementation, advanced capabilities like conditions and policy variables, and practical examples to help administrators and engineers securely manage access in ActiveScale environments.
IAM Feature Comparison Matrix (ActiveScale Versions)
| Feature/ActiveScale Version | 6.5 | 7.0 | 7.1 and above |
|---|---|---|---|
|
IAM Support |
No |
Yes |
Yes |
|
ACL Support |
Yes |
Yes (deprecated) |
Yes (deprecated) |
|
Policy Conditions |
No |
No |
Yes |
-
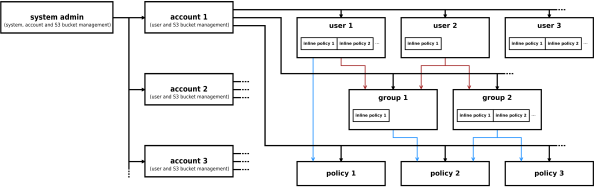
System Admin: Manages accounts, users, and S3 buckets.
-
Accounts: Containers for users, groups, and resources.
-
Users: Individuals who can have inline policies or belong to groups.
-
Groups: Collections of users. Groups can have inline or attached policies.
-
IAM Policies: JSON-based permission documents that define Allow or Deny rules. These can be attached to users, groups, or buckets.
Before diving into IAM Setup, it is essential to understand how IAM policies are evaluated in ActiveScale. This helps avoid confusion about precedence between different policy types.
Key Principles:
-
No hierarchy between policies: Bucket policies, user policies, and group policies are all evaluated together. One does not override the other.
-
Default = Deny: By default, all actions are denied unless explicitly allowed.
-
Explicit Deny wins: If any policy attached to a user, group, or bucket contains an explicit Deny, the action will be denied.
-
Allow applies only if no Deny exists: An action is permitted only if there is an explicit Allow and no matching Deny.
Example of Policy Evaluation:
Suppose we have a bucket my-example-bucket and an object inside it my-object.txt:
-
Bucket Policy: Allows
s3:GetObjecton all objects inmy-example-bucket/*. -
Group Policy: Denies
s3:GetObjectfor the group that includes the user. -
User Policy: No explicit statements about
s3:GetObject.
Result: The Deny from the group policy takes precedence. The user cannot perform s3:GetObject, even though the bucket policy allowed it.
2.0 IAM Setup
This section covers everything needed to prepare ActiveScale and your client environment to use Identity and Access Management (IAM).
We will be using AWS CLI to make IAM calls (explained in sections below). To enable AWS CLI access to make s3 and IAM calls, we need Fully Qualified Domain Name (FQDN) that resolves to your ActiveScale system. In case of S3, setting up domain name is optional as it can use the IP address in the host header, but in the case of IAM, IP addresses won’t work.
Good Practices for Choosing IAM Domain Name:
It is recommended to have the “iam” prefix for the FQDN, for example iam.activescale-system.your-domain where activescale-system is the identifier for the system and your-domain is the domain of the network.
To configure an IAM domain:
-
Click Configuration > System in the ActiveScale System Management Interface (SMI).
-
Scroll down to the Object Storage section.
-
Click Add Domain for IAM.
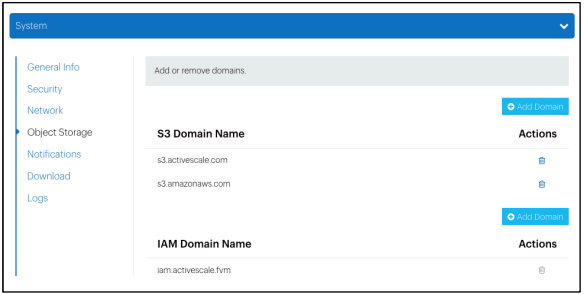
-
Ask your network administrator to make sure the IAM domain is reachable.
-
Use the ActiveScale System Management Interface (SMI) to create an account. The ActiveScale Admin creates an account by adding the account username and email address in the SMI, which generates the access key and secret key pair.
-
Save these credentials securely - they allow full IAM access within that account.
-
Add User to the account and generate the access keyand secret key.
Note: These credentials will be used in your AWS CLI profile root user and regular user.
-
Install AWS CLI (v2.22.35)
-
To install the latest version, follow the official AWS instructions: https://docs.aws.amazon.com/cli/latest/userguide/getting-started-install.html
aws configure --profile root-user
Enter credentials generated for root user in step 2.1 above:
-
Access Key ID:
<generated access key> -
Secret Access Key:
<generated secret key> -
Region:
us-east-1 -
Output: json
aws configure --profile demo-user
Enter credentials generated for user in step 2.1 above:
-
Access Key ID: (from user)
-
Secret Access Key: (from root user)
-
Region:
us-east-1 -
Output: json
3.0 IAM Policy Implementation (Replacing ACLs)
Before diving into individual policies, it's important to understand how access control shifts from ACLs to IAM in ActiveScale 7.x:
-
The root user of an ActiveScale account has FULL_CONTROL by default — it can perform any action on any resource.
-
A newly created regular IAM user has no access unless explicitly granted via policies.
The following table summarizes authorization changes that occurred when migrating from ActiveScale 6.5 to 7.x:
| Area | 6.5 Behavior | 7.x Behavior | Recommendation |
|---|---|---|---|
|
Default User Authorizations |
Users could by default perform certain bucket-level calls on parent account–owned buckets. |
Bucket ACLs with grants for users are no longer supported (only for accounts)
|
If access is required, grant it explicitly via identity policy or bucket policy. |
|
ACL READ Permissions |
READ ACLs authorized calls such as |
These calls are no longer authorized by READ ACLs. |
Provide explicit IAM policies if needed. |
|
ACL WRITE Permissions |
WRITE ACLs authorized calls such as |
These calls are no longer authorized by WRITE ACLs. |
Provide explicit IAM policies if needed. |
The following section maps traditional ACL permissions to IAM policies and shows how to write, attach, and test them.
|
ACL Permission |
Bucket-Level IAM Actions |
Object-Level IAM Actions |
|---|---|---|
|
READ |
|
|
|
WRITE |
|
|
|
READ_ACP |
|
|
|
WRITE_ACP |
|
|
|
FULL_CONTROL |
All of the above |
All of the above |
The table suggests that in ActiveScale 6.5, if you assign an ACL with READ permission to a regular user, it could perform a combination of bucket-and object-level s3 actions:
-
s3:ListBucket -
s3:ListAllmyBucket -
s3:ListBucketVersions -
s3:ListBucketMultipartUploads -
s3:ListMultipartUploadParts -
s3:GetObject -
S3:GetObjectVersion -
s3:GetObjectVersionForReplication
IAM policies in ActiveScale follow the same format as AWS, and are written in JSON format.
Each policy contains one or more statements that define:
-
Effect: Whether to Allow or Deny the action.
-
Action: The specific API calls being allowed or denied (e.g.,
s3:ListBucket,s3:GetObject). -
Resource: The ARN (Amazon Resource Name) of the bucket or object the action applies to.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "optionalStatementId",
"Effect": "<Allow or Deny>",
"Action": [
"<Action1>",
"<Action2>"
],
"Resource": [
"arn:aws:s3:::<bucket name>",
"arn:aws:s3:::<bucket name/object_name>"
]
}
]
}Fields explanation:
| Version: |
IAM policy language version. Always use 2012-10-17 to ensure support for modern IAM features. Older versions like 2008-10-17 do not support IAM conditions, IAM policy variables etc. |
| Statement: | Container of one or more policy rules. |
| Sid: | Optional. A unique statement identifier. Displayed when policies are listed for any IAM entity. |
| Effect: | Defines whether the listed actions are explicitly allowed (Allow) or denied (Deny). |
| Action: |
The specific API operations this statement applies to (e.g., |
| Resource: | The resources that the actions apply to, specified by their ARN (bucket or object). |
This structure allows you to group multiple actions under one statement and apply them to one or more resources.
In ActiveScale 6.5, if you assigned an ACL with READ to a regular user, it could:
-
List the contents of the bucket (
s3:ListBucket) -
Download objects from the bucket (
s3:GetObject) -
Retrieve object versions (
s3:GetObjectVersion) -
And could also perform
s3:ListBucketVersions,s3:ListBucketMultipartUploads,s3:ListMultipartUploadParts,s3:GetObjectVersionForReplication
To achieve the same result in 7.x using IAM, the user must be assigned a policy that includes all those actions.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetObject",
"s3:GetObjectVersion",
"s3:ListBucketVersions",
"s3:ListBucketMultipartUploads",
"s3:ListMultipartUploadParts",
"s3:GetObjectVersion",
"s3:GetObjectVersionForReplication"
],
"Resource": [
"arn:aws:s3:::testbucket1",
"arn:aws:s3:::testbucket1/*"
]
}
]
}
Each permission above can be attached separately, helping us achieve granularity in permissions using the following structure:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::testbucket1"
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*"
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::testbucket1/*"
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::testbucket1/*"
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetBucketAcl",
"s3:GetObjectAcl",
"s3:PutBucketAcl",
"s3:PutObjectAcl"
],
"Resource": [
"arn:aws:s3:::testbucket1",
"arn:aws:s3:::testbucket1/*"
]
}
]
}
You can attach the policy using AWS CLI’s put-user-policy command.
aws --profile root-user --endpoint-url https://iam.activescale.com iam put-user-policy \
--user-name demo-user \
--policy-name <PolicyName> \
--policy-document file://<path of policy file>
4.0 Practical Example: Setting Up Account, Users & Group Permissions
This section provides a practical walk through of creating different types of IAM users and attaching specific policies to them, demonstrating the concepts covered in previous sections.
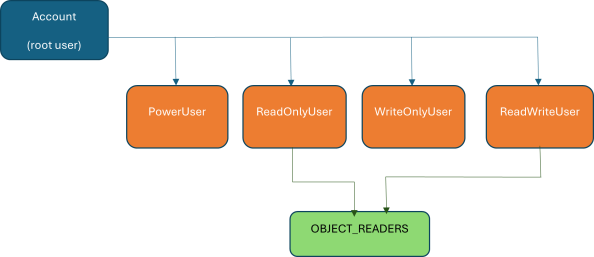
Account Structure for this Example:
| PowerUser: |
User with access similar to root user. |
| ReadOnlyUser: |
User with |
| WriteOnlyUser: |
User with only |
| ReadWriteUser: |
User with both |
| OBJECT_READERS: |
IAM group with |
Note: For this example, we will assume a bucket named my-example-bucket exists. You can replace this with your actual bucket name.
As mentioned above, the ActiveScale Admin creates the account. The first step is to create your ActiveScale account using the System Management Interface (SMI) and generate the root user access key and secret key. This root user will be used to manage all other IAM users and policies.
Configure AWS CLI profile for the root user using their credentials.
aws configure --profile root-user
-
Log in to the ActiveScale SMI with your root user credentials.
-
Navigate to Accounts > Accounts and User Management.
-
Click Add User.
-
Enter the required details for a new user (poweruser).
-
Generate and securely save the access key and secret key for poweruser.
-
Configure an AWS CLI profile for poweruser using their credentials:
aws configure --profile Poweruser
The PowerUser policy grants full administrative permissions on all resources within the account, similar to the root user's capabilities. Create a JSON file (e.g., poweruser-policy.json) with the following content:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
| "Action": "*": | Grants permission for all possible actions. |
| "Resource": "*": | Applies these permissions to all resources. |
Attach the poweruser-policy.json to the poweruser using the root user's CLI profile:
aws --profile root-user --endpoint-url https://iam.activescale.com iam put-user-policy \
--user-name poweruser \
--policy-name PowerUserAccess \
--policy-document file://poweruser-policy.json
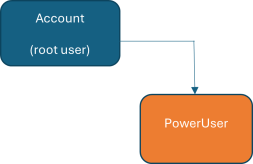
An account and a poweruser have now been created.
-
Create ReadOnlyUser via the ActiveScale System Management Interface (SMI):
-
Log in to the ActiveScale SMI.
-
Navigate to Accounts > Accounts and User Management.
-
Click Add User.
-
Enter details for readonlyuser.
-
Generate and securely save their access key and secret key.
-
Configure an AWS CLI profile for readonlyuser.
aws configure --profile readonlyuser
-
-
Write the Policy for ReadOnlyUser:
Create a JSON file (e.g.,
readonly-policy.json) that grants read-only permissions tomy-example-bucket.Copy{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetObject",
"s3:GetObjectVersion",
"s3:ListBucketVersions",
"s3:ListBucketMultipartUploads",
"s3:ListMultipartUploadParts",
"s3:GetObjectVersion",
"s3:GetObjectVersionForReplication"
],
"Resource": [
"arn:aws:s3:::my-example-bucket",
"arn:aws:s3:::my-example-bucket/*"
]
}
]
} -
Attach the Policy for ReadOnlyUser:
Attach the
readonly-policy.jsonto the readonlyuser using the root user's CLI profile:Copyaws --profile root-user --endpoint-url https://iam.activescale.com iam put-user-policy \
--user-name readonlyuser \
--policy-name ReadOnlyAccess \
--policy-document file://readonly-policy.json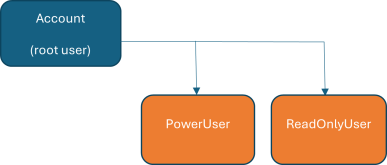
The poweruser and ReadOnlyUser have now been created.
-
Create WriteOnlyUser via the ActiveScale System Management Interface (SMI):
-
Follow the same steps as for readonlyuser to create a new user named writeonlyuser and configure their AWSCLI profile.
aws configure --profile writeonlyuser
-
-
Write the Policy for WriteOnlyUser:
Create a JSON file (e.g.,
writeonly-policy.json) that grants write-only permissions tomy-example-bucket.Copy{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:DeleteObject",
"s3:ReplicateDelete",
"s3:ReplicateObject",
"s3:DeleteObjectVersion"
],
"Resource": [
"arn:aws:s3:::my-example-bucket",
]
}
]
} -
Attach the Policy for WriteOnlyUser:
Attach the
writeonly-policy.jsonto thewriteonlyuserusing the root user's CLI profile:Copyaws --profile root-user --endpoint-url https://iam.activescale.com iam put-user-policy \
--user-name writeonlyuser \
--policy-name WriteOnlyAccess \
--policy-document file://writeonly-policy.json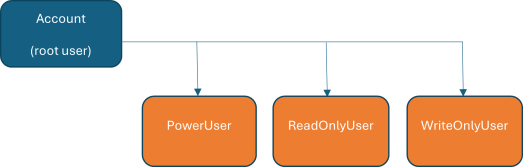
The Account, PowerUser, ReadOnlyUser and WriteOnlyUser have now been created.
-
Create ReadWriteUser via the ActiveScale System Management Interface (SMI):
-
Follow the same steps as for previous users to create a new user named readwriteuser and configure their CLI profile.
aws configure --profile readwriteuser
-
-
Write the Policy for ReadWriteUser:
Create a JSON file (e.g.,
readwrite-policy.json) that grants both read and write permissions tomy-example-bucket.Copy{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetObject",
"s3:GetObjectVersion",
"s3:ListBucketVersions",
"s3:ListBucketMultipartUploads",
"s3:ListMultipartUploadParts",
"s3:GetObjectVersion",
"s3:GetObjectVersionForReplication",
"s3:PutObject",
"s3:DeleteObject",
"s3:ReplicateDelete",
"s3:ReplicateObject",
"s3:DeleteObjectVersion"
],
"Resource": [
"arn:aws:s3:::my-example-bucket",
"arn:aws:s3:::my-example-bucket/*"
]
}
]
}This policy combines the actions from the ReadOnlyUser and WriteOnlyUser policies.
-
Attach the Policy for ReadWriteUser:
Attach the
readwrite-policy.jsonto thereadwriteuserusing the root user's CLI profile:Copyaws --profile root-user --endpoint-url https://iam.activescale.com iam put-user-policy \
--user-name readwriteuser \
--policy-name ReadWriteAccess \
--policy-document file://readwrite-policy.json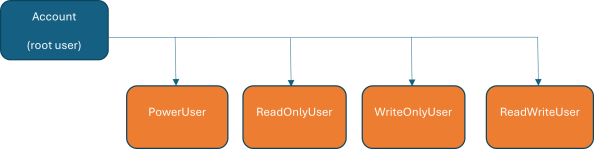
You now have an Account with PowerUser, ReadOnlyUser, WriteOnlyUser and ReadWriteUser with their respective policies attached.
This step demonstrates how to use IAM groups to manage permissions for multiple users efficiently.
-
Create the
OBJECT_READERSGroup:Create an IAM group named
OBJECT_READERSusing the AWS CLI:aws --profile root-user iam create-group --group-name OBJECT_READERS --endpoint-url https://iam.activescale.com -
Add Users to the
OBJECT_READERSGroup:Add readonlyuser and readwriteuser to the newly created
OBJECT_READERSgroup:aws --profile root-user iam add-user-to-group --group-name OBJECT_READERS --user-name readonlyuser --endpoint-url https://iam.activescale.com -
Write the Group Policy for
OBJECT_READERS:Create a JSON file (e.g., obj-
readers-group-policy.json). This policy will grantREADpermission for object levelIAM actions and it will be attached to the group.Copy{{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:GetObjectVersion",
"s3:GetObjectVersionForReplication"
],
"Resource": [
"arn:aws:s3:::testbucket1",
"arn:aws:s3:::testbucket1/*"
]
}
]
} -
Attach the Policy to the
OBJECT_READERSGroup:Attach the obj-
readers-group-policy.jsonto theOBJECT_READERSgroup using the root user's CLI profile:aws iam put-group-policy --group-name OBJECT_READERS --policy-name ObjReadersAccessPolicy --policy-document file://obj-readers-group-policy.json --profile root-user --endpoint-url https://iam.activescale.com
Now, any user who is a member of the OBJECT_READERS group will inherit these object level IAM read permissions.
5.0 IAM Policies: Advanced Features
ActiveScale 7.1 introduces advanced features for IAM policies, including conditions and policy variables, which allow for more granular and dynamic control over access.
Conditions are an optional element within IAM policy statements that enable highly granular and dynamic control over permissions. They specify when a policy should be applied based on contextual factors of a request.
Benefits of using Conditions:
-
Precise Control: Limit permissions to specific scenarios.
-
Context-Aware Access: Control access based on request attributes like IP address, time of day, or specific object metadata.
-
Attribute-Based Access Control (ABAC): Restrict access based on the presence or absence of certain attributes in the request.
Syntax for IAM Conditions:
Conditions are defined within a policy statement using the following structure:
"Condition": {
"{condition-operator}" : {
"{condition-key}" : "{condition-value}"
}
}
This policy allows s3:PutObject only if the aws:username in the request context is johndoe.
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": ["s3:PutObject"],
"Resource": "arn:aws:s3::*:bucket-1/object",
"Condition": {
"StringEquals": {"aws:username": "johndoe"}
}
}
}
In the example above “StringEquals” is the condition operator uses. ActiveScale implements all standard AWS IAM condition operators. These operators are used to match the condition key and value defined in the policy against the corresponding values in the request context. The choice of operator depends on the data type of the condition key.
Common categories of condition operators include:
| String Operators: |
|
| Numeric Operators: |
|
| Boolean Operators: |
|
| Null Operator: |
|
| Date Operators: |
|
| Binary Operators: | BinaryEquals
|
| IP Address Operators: |
|
| ARN Operators: |
|
You can use multiple condition operators within the same Condition block. When multiple operators are present at the same level, they are evaluated with an AND logic.
Example: This policy requires both the username to be johndoe AND the source IP address to be 172.10.21.12.
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": ["s3:PutObject"],
"Resource": "arn:aws:s3::*:bucket-1/object",
"Condition": {
"StringEquals": {"aws:username": "johndoe"},
"IpAddress": {"aws:SourceIP": "172.10.21.12"}
}
}
}
Condition keys are key-value pairs that allow you to define specific scenarios under which a policy is applied. They represent attributes of the request, resource, or user.
-
AWS Global Keys: These keys are available in all AWS services (and ActiveScale IAM). Examples include
aws:CurrentTimeandaws:SourceIP. -
Service-Specific Keys: These keys are unique to a particular service. For S3, examples include
s3:x-amz-storage-classands3:prefix. For IAM, an example isiam:PolicyARN.
If a condition key used in a policy is not present in the request context, the condition typically evaluates to false. However, you can modify this behavior using the ...IfExists suffix.
...IfExists Operator:
You can append IfExists to the end of any condition operator name (except Null).
-
If the condition key is not present in the request context, the condition evaluates to
true.-
Example:
"StringEqualsIfExists": {"aws:invalid": "johndoe"}(Ifaws:invalidis not in the request, this condition passes).
-
-
If the condition key is present, the key is processed as specified in the policy.
-
Example:
"StringEqualsIfExists": {"aws:username": "johndoe"}(Ifaws:usernameis present, it must equal johndoe).
-
-
Multiple Condition Keys within an Operator:
You can specify multiple condition keys within a single condition operator. These are evaluated with an AND logic.
-
Example:
Copy"Condition": {
"StringEquals": {
"aws:username": "johndoe",
"s3:versionid": "version-1"
}
}(Requires
aws:usernameto be "johndoe" ANDs3:versionidto be "version-1")
-
-
Multiple Condition Values for a Key:
You can specify multiple condition values for a single condition key. These are evaluated with an OR logic.
-
Example:
Copy"Condition": {
"StringEquals": {
"aws:username": ["bob", "alice"]
}
}(Requires
aws:usernameto be "bob" OR "alice")
-
-
Within a single condition operator (e.g.,
StringEquals):-
Multiple
context keysareANDed. -
Multiple
valuesfor a single context key areORed.
-
-
Across different condition operators within the
Conditionblock:-
Each condition operator block is
ANDed together.
-
-
Negated Operators: Operators like
StringNotEqualsorNumericNotEqualsreverse the matching logic.
Policy variables act as placeholders that you can use in your IAM policies when the exact value of a resource or condition key is not known at the time the policy is written. They are dynamically evaluated at the time of the request.
Policy variables are enclosed in ${...} and typically contain a condition key inside, for example: ${aws:username}. They can be used within both the Resource and Condition fields of a policy.
Example: User-Specific Object Prefix
This policy can be set for a group to allow every user to put objects only with their username as a prefix in the bucket.
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": ["s3:PutObject"],
"Resource": "arn:aws:s3:::demo-bucket-001/${aws:username}/*"
}
}
In this example, ${aws:username} will be replaced by the actual username of the requesting user at runtime.
If the condition key used within a policy variable is not present in the request context, the policy statement evaluates to false.
You can specify a default value to be used if the condition key for the policy variable is not present. This is done by adding a comma-separated default value within the curly braces.
Example:
"Resource": "arn:aws:s3:::demo-bucket-001/${aws:invalid, 'object-1'}"
If aws:invalid is not available in the request context, object-1 will be used as the prefix.
There are special policy variables for characters that otherwise have special meaning in JSON :
-
${*}: Use where you need an asterisk (*) character.
-
${?}: Use where you need a question mark (?) character.
-
${$}: Use where you need a dollar sign ($) character.
Example:
If you have an object named my_file*backup.txt and you want to grant access to it specifically:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::demo-bucket-01/my_file${*}backup.txt"
}
]
}
This policy will match my_file*backup.txt exactly, if we don’t use policy variable in this case it will allow access to all files that match: my_file<any-text-here>-backup.txt.
6.0 AWS IAM API Compatibility
The ActiveScale IAM API is compatible with the AWS IAM API, though not all AWS features are supported. The full AWS IAM API can be found here, this document details the difference in supported features as well as some basic examples to help you get started.
| Actions | Notes |
|---|---|
| Version | Only version “2012-10-17” is supported by ActiveScale IAM. For more information on IAM version refer to the AWS documentation. |
| Statement.Principal |
Note: Only for bucket policies. Supported principal types:
|
| Statement.NotPrincipal | Refer to Statement.Principal. |
| Action |
|
| NotAction | Refer to Action. |
| Resource |
|
| NotResource | Refer to Resource. |
| Condition | Supported from ActiveScale 7.1 and above. |
| ? | Match one character. For example “arn:aws:s3:::bucket?” matches “arn:aws:s3::bucket1” and “arn:aws:s3:buckets” but not “arn:aws:s3::bucket123”. |
| * | Match any number of characters. For example “arn:aws:s3:::bucket*” matches “arn:aws:s3::bucket1”, “arn:aws:s3:buckets” and “arn:aws:s3::bucket123”. |
Supported from ActiveScale 7.1 and above.
The following tables list the support actions supported by ActiveScale IAM and any difference with AWS IAM. For more in-depth information on the actions please refer to the AWS documentation.
| Actions | Request Parameters | Response Elements |
|---|---|---|
| CreateAccessKey |
Supported request parameters:
|
Supported response elements:
Not supported response elements:
|
| ListAccessKeys |
Supported request parameters:
|
Supported response elements:
|
| UpdateAccessKey |
Supported request parameters:
|
Status Supported response elements:
|
| Actions | Request Parameters | Response Elements |
|---|---|---|
| CreateGroup |
Supported request parameters:
|
Supported response elements:
|
| GetGroup |
Supported request parameters:
|
Supported response elements:
|
| ListGroups |
Supported request parameters:
|
Supported response elements:
|
| UpdateGroup |
Supported request parameters:
|
Supported response elements:
|
| DeleteGroup |
Supported request parameters:
|
Supported response elements:
|
| AddUserToGroup |
Supported request parameters:
|
Supported response elements:
|
| ListGroupsForUser |
Supported request parameters:
|
Supported response elements:
|
| RemoveUserFromGroup |
Supported request parameters:
|
Supported response elements:
|
| Actions | Request Parameters | Response Elements |
|---|---|---|
| PutGroupPolicy |
Supported request parameters:
|
Supported response elements:
|
| GetGroupPolicy |
Supported request parameters:
|
Supported response elements:
|
| ListGroupPolicies |
Supported request parameters:
|
Supported response elements:
|
| DeleteGroupPolicy |
Supported request parameters:
|
Supported response elements:
|
| AttachGroupPolicy |
Supported request parameters:
|
Supported response elements:
|
| ListAttachedGroupPolicies |
Supported request parameters:
|
Supported response elements:
|
| DetachGroupPolicy |
Supported request parameters:
|
Supported response elements:
|
| Actions | Request Parameters | Response Elements |
|---|---|---|
| CreatePolicy |
Supported request parameters:
Description Not supported request parameters:
|
Supported response elements:
Not supported response elements:
|
| GetPolicy |
Supported request parameters:
|
Supported response elements:
Not supported response elements:
|
| ListPolicies |
Supported request parameters:
|
Supported response elements:
Not supported response elements:
|
| DeletePolicy |
Supported request parameters:
|
Supported response elements:
|
| Actions | Request Parameters | Response Elements |
|---|---|---|
| CreatePolicyVersion |
Supported request parameters:
|
Supported response elements:
|
| GetPolicyVersion |
Supported request parameters:
|
Supported response elements:
|
| ListPolicyVersions |
Supported request parameters:
|
Supported response elements:
|
| DeletePolicyVersion |
Supported request parameters:
|
Supported response elements:
|
| SetDefaultPolicyVersion |
Supported request parameters:
|
Supported response elements:
|
| Actions | Request Parameters | Response Elements |
|---|---|---|
| CreateUser |
Supported request parameters:
Not supported requests parameters:
|
Supported response elements:
|
| GetUser |
Supported request parameters:
|
Supported response elements:
Not supported response elements:
|
| ListUsers |
Supported request parameters:
|
Supported response elements:
Not supported response elements:
|
| UpdateUser |
Supported request parameters:
|
Supported response elements:
|
| DeleteUser |
Supported request parameters:
|
Supported response elements:
|
| Actions | Request Parameters | Response Elements |
|---|---|---|
| PutUserPolicy |
Supported request parameters:
|
Supported response elements:
|
| GetUserPolicy |
Supported request parameters:
|
Supported response elements
|
| ListUserPolicies |
Supported request parameters:
|
Supported response elements:
|
| DeleteUserPolicy |
Supported request parameters:
|
PolicyName Supported response elements:
|
| AttachUserPolicy |
Supported request parameters:
|
PolicyArn Supported response elements:
|
| ListAttachedUserPolicies |
Supported request parameters:
|
Supported response elements:
|
| DetachUserPolicy |
Supported request parameters:
|
Supported response elements:
|
| Condition Key | Description |
|---|---|
|
aws:CurrentTime |
Current time in ISO8601 format. |
|
aws:EpochTime |
The date in epoch or Unix time. |
|
aws:PrincipalAccount |
The account id to which the principal belongs. |
|
aws:PrincipalArn |
The ARN of the principal. |
|
aws:PrincipalType |
Indicates whether the principal is an account or user ("Account", "User", "Anonymous"). |
|
aws:SecureTransport |
Boolean value that represents whether the request was sent using SSL. |
|
aws:SourceIp |
The requester's IP address. |
|
aws:UserAgent |
Information about the requester's client application. |
|
aws:userid |
(if "Account"), unique user id (if "User") or not set (if "Anonymous"). |
|
aws:username |
The friendly name of the current user (only set for principal type "User"). |
| Condition Key | Description |
|---|---|
|
iam:PolicyARN |
ARN of a managed policy in requests that involve a managed policy. |
| Condition Key | Description |
|---|---|
|
s3:LocationConstraint |
The region. |
|
s3:ResourceAccount |
The owner account id of the resource (bucket). |
|
s3:TlsVersion |
The TLS version used by the client. |
|
s3:VersionId |
The object version id. |
|
s3:authType |
The authentication method ("REST-HEADER", "REST-QUERY-STRING", "POST"). |
|
s3:delimiter |
The delimiter parameter of the request. |
|
s3:max-keys |
The max-keys parameter of the request. |
|
s3:object-lock-legal-hold |
The object legal hold status. |
|
s3:object-lock-mode |
The object retention mode ("COMPLIANCE", "GOVERNANCE"). |
|
s3:object-lock-remaining-retention-days |
The remaining object retention days. |
|
s3:object-lock-retain-until-date |
The object retain until date. |
|
s3:prefix |
The prefix parameter of the request. |
|
s3:signatureAge |
The age (in ms) of the request signature. |
|
s3:signatureversion |
The signature version ("AWS" for v2, "AWS4-HMAC-SHA256" for v4). |
|
s3:x-amz-acl |
The canned ACL from the request x-amz-acl header. |
|
s3:x-amz-content-sha256 |
Set to "UNSIGNED-PAYLOAD" if the payload isn't signed. |
|
s3:x-amz-copy-source |
The copy source (bucket, prefix, object) for a copy request. |
|
s3:x-amz-grant-full-control |
The request x-amz-grant-full-control header. |
|
s3:x-amz-grant-read |
The request x-amz-grant-read header. |
|
s3:x-amz-grant-read-acp |
The request x-amz-grant-read-acp header. |
|
s3:x-amz-grant-write |
The request x-amz-grant-write header. |
|
s3:x-amz-grant-write-acp |
The request x-amz-grant-write-acp header. |
|
s3:x-amz-metadata-directive |
The request x-amz-metadata-directive header. |
|
s3:x-amz-server-side-encryption |
The request x-amz-server-side-encryption header. |
|
s3:x-amz-storage-class |
The request x-amz-storage-class header. |
|
s3:x-amz-website-redirect-location |
The request x-amz-website-redirect-location header. |
| Resource | Max Value |
|---|---|
| Managed policy size: | 6144 bytes (whitespace ignored) |
| User policy size: | 2048 bytes (whitespace ignored) |
| Attached policies per user: | 20 |
| Group policy size: | 5120 bytes (whitespace ignored) |
| Attached policies per group: | 10 |
| Number of access keys per IAM user: | 2 |
| Total number of accounts: | 10000 |
| Total number of users per account: | 5000 |
| Total number of groups per account: | 500 |
| Number of groups a user can be attached to: | 10 |
| Number of users per group: | 5000 |
| Number of managed policies per account: | 5000 |
| Number of policy versions: | 5 |
7.0 Granting READ Access for System Bucket
By default, no account/user has READ permission for System Bucket. Granting READ access to a system bucket depends on the type of user:
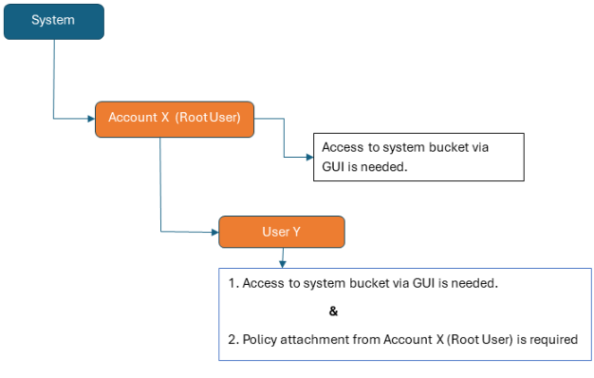
Root users can be granted access using only the ActiveScale System Management Interface (SMI).
-
Go to: Accounts > System Bucket
-
Click Grant Read Access
-
Enter the root user's email address
-
Click Grant
Access is immediately available. The name of the system bucket appears under System Bucket Info in the SMI.
Regular users require two steps:
-
Grant via GUI (Accounts > System Bucket): This registers their email/user in the GUI, as mentioned in the previous section for Root user.
-
Attach IAM Access Policy: From the parent account/root user, attach IAM policy granting the user,
READaccess to the system bucket
Example IAM user Policy for System Bucket:
Note the System bucket name in system bucket info is system-719f8f91-71ad-4970-87cb-927b6cd71f0a
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetObject",
"s3:GetObjectVersion"
],
"Resource": [
"arn:aws:s3::: system-719f8f91-71ad-4970-87cb-927b6cd71f0a",
"arn:aws:s3::: system-719f8f91-71ad-4970-87cb-927b6cd71f0a/*"
]
}
]
}
8.0 Policies & AWS CLI Usage Examples
It is not recommended to perform day-to-day operations as the account root user. Instead, create a user with the minimum required permissions for day-to-day operations. For example, you could create an administrative user who can be used to set permissions for other users, but who cannot perform any S3 calls. Keep in mind that permissions can be set on a subset of resources by using the appropriate wildcards.
You cannot limit the permissions of the account's root user, who has all permissions by default. Quantum advises to only use the root user's credentials for initially setting up and carrying over permissions to an administrative user (group), and then removing or disabling the root user's access keys. Malicious use of (leaked) access keys can then always be rapidly stopped by a DenyAll policy for the User owning the access keys.
In emergency cases, access keys may also be disabled or deleted through the GUI by the system administrator, and new access keys can be created for the account's root user.
This section provides a collection of various IAM policy examples to illustrate different access control scenarios and how they can be achieved using ActiveScale IAM.
This policy grants a user or group permission to perform all IAM operations on all IAM resources.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "allowAllIam",
"Effect": "Allow",
"Action": "iam:*",
"Resource": "*"
}
]
}
This policy allows PutObject and GetObject actions only on objects with the prefix "engineering/" within the "my-corporation" bucket.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "restrictedPutGet",
"Effect": "Allow",
"Action": ["s3:PutObject", "s3:GetObject"],
"Resource": "arn:aws:s3:::my-corporation/engineering/*"
}
]
}
This policy allows all S3 operations on the "main-bucket" and its objects, except for those S3 operations that start with "Delete".
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "allowAllS3ObjectActionsExceptDelete",
"Effect": "Allow",
"NotAction": "s3:Delete*",
"Resource": "arn:aws:s3:::main-bucket/*"
},
{
"Sid": "allowAllS3BucketActionsExceptDelete",
"Effect": "Allow",
"NotAction": "s3:Delete*",
"Resource": "arn:aws:s3:::main-bucket"
}
]
}
This group policy allows access to the "exam-results" bucket only for users "alice" and "bob" within the same group, while denying access to other users.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowAliceAndBob",
"Effect": "Allow",
"Action": "*",
"Resource": [
"arn:aws:s3:::exam-results"
],
"Condition": {
"StringEquals": {
"aws:username": ["alice", "bob"]
}
}
}
]
}
This group policy allows access to all users, but only for objects that have their username as a prefix within the "exam-results" bucket.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": [
"arn:aws:s3:::exam-results/${aws:username}/*"
]
}
]
}
This bucket policy, applied to the "exam-results" bucket, denies access to all users belonging to account "123456789012" within the "students" path.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "noStudents",
"Effect": "Deny",
"Principal": {
"AWS": "arn:aws:iam::123456789012:students/*"
},
"Action": "*",
"Resource": ["arn:aws:s3:::exam-results", "arn:aws:s3:::exam-results/*"]
}
]
}
This policy explicitly denies all S3 actions if the request originates from a specific IP address range (e.g., 192.0.2.0/24). This is useful for restricting access to trusted networks.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "s3:*",
"Resource": "*",
"Condition": {
"IpAddress": {
"aws:SourceIp": "192.0.2.0/24"
}
}
}
]
}
This policy allows users to perform S3 actions only during specified time window.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": "*",
"Condition": {
"DateGreaterThan": {
"aws:CurrentTime": "2025-07-31T09:00:00Z"
},
"DateLessThan": {
"aws:CurrentTime": "2025-07-31T17:00:00Z"
},
"StringEquals": {
"aws:RequestedRegion": "us-east-1"
}
}
}
]
}
Note: The aws:CurrentTime condition uses a specific date for demonstration. In a real-world scenario, you would typically use aws:CurrentTime with only time components or combine it with aws:CurrentDate for daily recurring checks.
This policy denies any S3 operation if the request is not made over a secure transport (HTTPS).
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "s3:*",
"Resource": "*",
"Condition": {
"Bool": {
"aws:SecureTransport": "false"
}
}
}
]
}
This policy allows PutObject only if the x-amz-acl header in the request is set to bucket-owner-full-control, ensuring new objects grant full control to the bucket owner.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::my-example-bucket/*",
"Condition": {
"StringEquals": {
"s3:x-amz-acl": "bucket-owner-full-control"
}
}
}
]
}
This policy allows a user to list objects within my-example-bucket but only if the request specifies the documents/ prefix.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::my-example-bucket",
"Condition": {
"StringEquals": {
"s3:prefix": "documents/"
}
}
}
]
}
This bucket policy, applied to my-example-bucket, grants s3:GetObject permission to a specific IAM user (external-user) in a different AWS account (123456789012). This is typically done via a bucket policy rather than a user policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:user/external-user"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::my-example-bucket/*"
}
]
}
Note: Replace 123456789012 with the actual external account ID and external-user with the actual external IAM user name.
This bucket policy, applied to bucket-001, allows a specific IAM user (user-002 in account 376342406769) to upload objects and set retention using s3:PutObject and s3:PutObjectRetention. However, it enforces that all objects must have a minimum retention period of 365 days in COMPLIANCE mode. Attempts to set retention shorter than 365 days will be denied.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::376342406769:user/user-002"
},
"Action": [
"s3:PutObject",
"s3:PutObjectRetention"
],
"Condition": {
"NumericGreaterThanEquals": {
"s3:object-lock-remaining-retention-days": 365
},
"StringEquals": {
"s3:object-lock-mode": "COMPLIANCE"
}
},
"Resource": "arn:aws:s3:::bucket-001/*"
}
]
}
The following code snippet shows the various users and groups interact with policies using AWS CLI. For more information on AWS CLI refer to the AWS documentation.
# Create a user called "demo-user"
~ $ aws --profile demo iam create-user --user-name demo-user
{
"User": {
"Path": "/",
"UserName": "demo-user",
"UserId": "AIDACCX78G1TZHCH0ATQ1",
"Arn": "arn:aws:iam::652303226922:user/demo-user",
"CreateDate": "2024-03-04T09:03:07+00:00"
}
}
# Add a new inline policy document to "demo-user"
# User policy is a local json file similar to the "Sample policy document" examples
~ $ aws --profile demo iam put-user-policy --user-name demo-user --policy-name my-policy --policy-document file://my-policy.json
# List and get the new inline policy
~ $ aws --profile demo iam list-user-policies --user-name demo-user
{
"PolicyNames": [
"my-policy"
]
}
~ $ aws --profile demo iam get-user-policy --user-name demo-user --policy-name my-policy
{
"UserName": "demo-user",
"PolicyName": "my-policy",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Sid": "allowAllIam",
"Effect": "Allow",
"Action": "iam:*",
"Resource": "*"
}
]
}
}
# Create a group of users, users of a group automatically have the permissions of the group
# on top of any permissions they already have (for example via in-line policies)
~ $ aws --profile demo iam create-group --group-name my-users
{
"Group": {
"Path": "/",
"GroupName": "my-users",
"GroupId": "AGPAYOKKRE1I380Y6UW6E",
"Arn": "arn:aws:iam::652303226922:group/my-users",
"CreateDate": "2024-03-04T09:24:35+00:00"
}
}
# Add our user to this group and list all users for this group
~ $ aws --profile demo iam add-user-to-group --user-name demo-user --group-name my-users
~ $ aws --profile demo iam get-group --group-name my-users
{
"Users": [
{
"Path": "/",
"UserName": "demo-user",
"UserId": "AIDA3FFSDMOUD3GJPUOE1",
"Arn": "arn:aws:iam::652303226922:user/demo-user",
"CreateDate": "2024-03-04T09:13:24+00:00"
}
],
"Group": {
"Path": "/",
"GroupName": "my-users",
"GroupId": "AGPAYOKKRE1I380Y6UW6E",
"Arn": "arn:aws:iam::652303226922:group/my-users",
"CreateDate": "2024-03-04T09:24:35+00:00"
}
}
# Groups can also have inline policies
~ $ aws --profile demo iam put-group-policy --group-name my-users --policy-name group-policy --policy-document file://group-policy.json
# When the same policy needs to applied to many different users or groups, we can create managed policies which can be re-used
~ $ aws --profile demo iam create-policy --policy-name reusable-policy --policy-document file://my-policy.json
{
"Policy": {
"PolicyName": "reusable-policy",
"PolicyId": "ANPA932LSXO1VC1W7XVZH",
"Arn": "arn:aws:iam::652303226922:policy/reusable-policy",
"Path": "/",
"DefaultVersionId": "v1",
"AttachmentCount": 0,
"IsAttachable": true,
"CreateDate": "2024-03-04T09:31:15+00:00",
"UpdateDate": "2024-03-04T09:31:15+00:00"
}
}
# This policy can now be attached to users and groups, the attached policy will be added on-top of any existing permissions
# When the policy is updated all attached users and groups will have their permissions updated as well
# In this example we only attach the policy to the group
~ $ aws --profile demo iam attach-group-policy --group-name my-user s --policy-arn "arn:aws:iam::652303226922:policy/reusable-policy"
~ $ aws --profile demo iam list-attached-group-policies --group-name my-users
{
"AttachedPolicies": [
{
"PolicyName": "reusable-policy",
"PolicyArn": "arn:aws:iam::652303226922:policy/reusable-policy"
}
]
}
Troubleshooting
-
AccessDenied: Implies missing IAM permission for the requesting user. Review the IAM policies for the user and assign the required permissions.
-
Still fails?: Check IAM permissions for the specified user. Check for the allowed and denied actions and resources in the policy.
